IMPORTANT!!!!
MYTH BUSTER
When you see the Myth Buster icon, it’s time to challenge commonly held beliefs! This marker highlights misconceptions or myths that might hold you back and replaces them with facts to set the record straight.
Example: “MYTH: You need a Master’s degree to start a cybersecurity career.”
ACTION ITEM

The Action Item icon signals a task or step you should take to move forward in your journey. These are practical, to-the-point actions designed to help you stay on track and achieve your goals.
Example: “ACTION ITEM: Create a LinkedIn profile optimized for the cybersecurity roles you’re targeting.”
WARNING

The Warning icon alerts you to potential pitfalls, risks, or mistakes to avoid. Pay close attention whenever you see this marker—it’s your early warning system to keep you from heading in the wrong direction!
Example: “WARNING: Don’t blindly accept a job offer without researching the company’s leadership and culture.”
TIP

The Tip icon offers valuable advice, quick shortcuts, or insights that can help you make smarter choices. Think of these as nuggets of wisdom curated to make your journey smoother and more efficient.
Example: “TIP: Use tools like Glassdoor and LinkedIn to cross-check employee reviews before applying for a job.”
These highlighters are here to guide you, whether it’s breaking myths, providing actionable steps, alerting you to risks, or sharing useful tips. Keep an eye out for them as you explore the blog, and let them enhance your learning experience!
1. What to Know Before Entering or Switching to Cybersecurity?
Three Main Components
- Understand the scale of the spectrum: Learn about the various domains within cybersecurity and what they are before choosing anything.
- Create & meet your requirements/needs: Define what you need to achieve your goals and map out your path. (Will give more options later on)
- Plan & execute it: Turn your learning and preparation into actionable steps.
Eight Steps of the Approach
- Keep doing your current job: If you are not working, skip to the next step.
- Research various cybersecurity domains: Explore the different areas of cybersecurity to find your interest.
- Prepare a study plan & study: Create a structured plan to gain relevant skills and knowledge.
- Enter the field: Take the first step into cybersecurity with confidence and only focus on some things rather than all.
- Find a mentor in cybersecurity: Seek guidance from someone experienced in the field.
- Apply for jobs : Focus on targeted job applications to roles that suit your skills with a structured approach.
- Congrats! Mission completed: Celebrate your journey and continue growing in your role.
Key Tip: Keep Doing Your Current Job


2. Which cybersecurity domain is the right fit for me?
Refer to the CISO Mind Map: Explore these resources to get an overview of cybersecurity domains that one large company CISO would handle:
Understand the Domains: Learn about the various domains available in cybersecurity. Each domain has unique responsibilities and skill requirements.

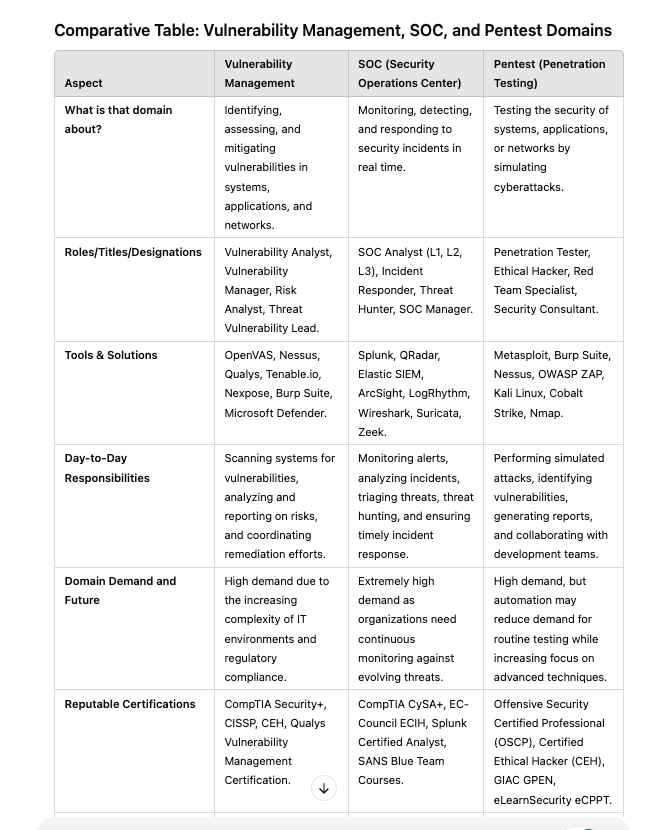
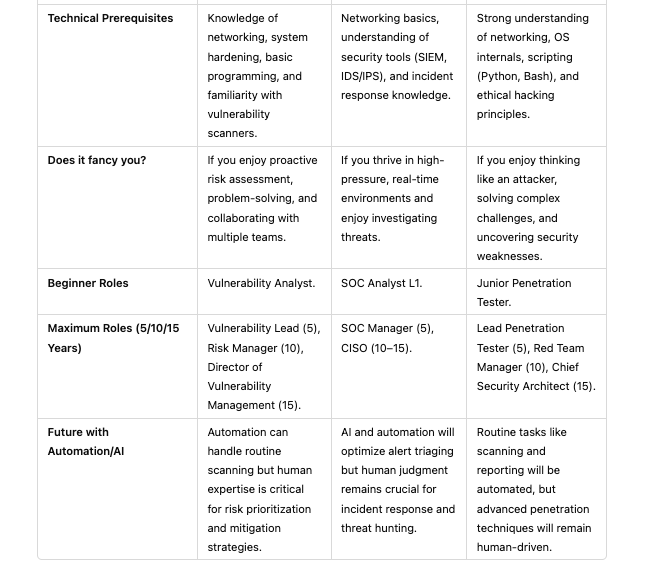
- What is that domain about?
- What kinds of roles/titles/designations does the company offer in that domain?
- What free, open-source, or commercial tools and solutions do people/companies use?
- What are the day-to-day roles and responsibilities in that job role?
- Is the domain demanding? What is its potential future?
- Which organizations provide reputable certifications for this domain?
- What are the technical prerequisites to enter this domain?
- Does it fancy you?
- Which roles you can start within that domain as beginer and where can you reach maximum after 5/10/15 years?
- What will be the future of this role in regards to automation and AI?

- Stay curious and use resources like Google or ChatGPT to gather more insights into each of these questions for any of your domains you are interested in like mentioned below.
3. What’s the best way to learn cybersecurity?
| Study Option | Why | Pros | Cons | Resources/How-to |
|---|---|---|---|---|
| Read a Book | Books provide comprehensive knowledge, taking you from beginner to advanced levels. | - Structured and detailed. - Learn at your own pace. - Encourages critical thinking. | - Time-consuming. - Some may lack practical experience. - Requires motivation and discipline. | - Use libraries or eBook platforms. - Search on Amazon, filter by “Publication Date.” - Start with beginner-friendly authors. |
| YouTube Playlist | Watch topic-focused videos for accessible and free learning. | - Free and flexible. - Wide variety of content. | - Quality and depth vary by creator. - Research required to find credible playlists. | - Search on YouTube with filters. - Look for structured playlists with recent uploads. |
| ChatGPT | Interact with AI for quick explanations or detailed guidance. | - Accessible and interactive. | - Depends on asking the right questions. - Some information might be outdated. | - Use AI platforms like OpenAI for Q&A sessions or brainstorming study plans. |
| Official Certification | Gain recognized proof of expertise that employers value. | - Highly respected. - Encourages goal-focused learning. | - Expensive. - Time-limited validity for some certifications. | - Explore certifications like CompTIA Security+, CEH, CISSP, or Offensive Security. |
| Online Courses (e.g., Udemy) | Structured, on-demand courses for various topics in cybersecurity. | - Covers specialized topics. - Access to multiple authors’ approaches. | - Quality varies by platform and instructor. - Paid courses may not always justify their cost. | - Use platforms like Udemy, Coursera, Pluralsight. - Check ratings and reviews before purchasing. |
| Self-Learning Projects | Apply theoretical knowledge in practical projects to solidify learning. | - Builds practical experience. | - Requires high motivation and time commitment. | - Identify personal projects related to cybersecurity and work on them consistently. |
| MOOCs (edX, Coursera) | Learn from top universities through online platforms. | - Free or affordable options. - Structured curriculum. | - Some lack certification options. | - Use edX or Coursera for cybersecurity courses. |
| Internships/Apprenticeships | Real-world job experience that helps build skills and connections. | - Hands-on learning. - Potential for full-time offers. | - Often unpaid or with low pay. - Quality of learning depends on the organization. | - Search LinkedIn or company websites for internships. |
| Podcasts | Engage with expert discussions while multitasking. | - Time-efficient. | - Depth and consistency vary by podcast. | - Listen to podcasts like Darknet Diaries or The CyberWire. |
| Peer Learning Groups | Collaborate with others for shared learning and motivation. | - Instant feedback and collaboration. | - Scheduling conflicts. | - Join study groups on Reddit, Discord, or LinkedIn communities. |
| Webinars/Workshops | Attend live learning sessions with industry experts. | - Opportunity to ask questions directly. | - Fixed schedules may not suit everyone. | - Participate in webinars hosted by cybersecurity professionals or organizations. |
| Social Media Learning | Follow relevant content creators and engage in discussions. | - Free, informal learning. | - Risk of misinformation or low-quality advice. | - Use LinkedIn, Twitter, or specialized cybersecurity communities for updates and interaction. |
| Freeform Study (Google/YouTube) | Use free resources to learn flexibly at your own pace. | - Free and vast range of content. | - Requires effort to filter reliable and useful sources. | - Research topics via Google and watch theory/practical videos on YouTube. |
4. How do I create a personalized career plan?
Time Management for Work-Life Balance: Balance your job, social life, and cybersecurity learning effectively.
Allocate Time for Learning
- Prepare a daily or weekly schedule.
- Set realistic targets to ensure consistent progress.
Two Ways to Create a Study Timetable:
- Fixed Time:
Suitable for those with a predictable weekly schedule. Dedicate specific days or hours to study. - Fixed Hours:
Ideal for those with shift jobs or variable schedules. Dedicate 1-3 hours to study when free.
- Fixed Time:
Use Tools to Plan Effectively

- Organize topics and track progress systematically.
Keep Your Plan Visible: Place your plan somewhere you see often (e.g., desk, fridge) to stay motivated.
Review and Adjust Regularly: Regularly assess your progress and tweak the plan as necessary.
Online Tools and Templates: Use online tools like Google Sheets for collaborative planning. Templates for Excel or Notion can simplify study tracking.
5. How do I research companies effectively during job hunting?
| Factor | What to Look For | Why It Matters |
|---|---|---|
| Revenue | Is the company financially stable and growing? | Indicates financial health and stability. |
| Company Size | Are the number of employees increasing? | A growing workforce reflects success and expansion. |
| Area of Focus | What is the company’s primary area of service? | Aligns your goals with their mission and core values. |
| Client Base | Who are their main clients? | Gives insight into your potential stakeholders and daily interactions. |
| Reviews and Feedback | What are employees saying on platforms like Glassdoor? | Highlights workplace culture and potential red flags. |
| Company Culture | Is the company inclusive? Does it promote work-life balance and employee well-being? | Helps gauge if the environment fits your expectations and values. |
| Leadership | Who are the CEO and key leaders? What’s their leadership style? | Leadership influences company vision and decision-making. |
| Future Plans | Does the company have a clear roadmap for innovation or market expansion? | Shows stability and growth potential. |
| Recent News | Has the company been in the news for positive or negative reasons? | Keeps you informed about the company’s reputation and current events. |
| Competitors | Who are the company’s main competitors, and how do they stand out? | Understanding the competitive landscape helps identify challenges and opportunities. |
| Values and Mission | Do their mission statement and values resonate with you? | Ensures alignment with your personal and professional principles. |
Prioritizing Your Needs

That’s why it’s crucial to prioritize. Choose at least 2–3 factors that matter the most to you, and if those are fulfilled, consider that company a good match. Remember, perfection is a myth—even in Silicon Valley.
| Criteria | What to Consider | Example |
|---|---|---|
| Career Growth | Does the company offer learning opportunities, certifications, or mentorship programs? | Sponsorship for certifications, conferences, or cross-functional training programs. |
| Compensation | Evaluate salary, bonuses, and benefits offered. | Stock options, remote work perks, and health insurance. |
| Team and Management | Research managers and team dynamics through LinkedIn. | Look for engaged and supportive leaders on social platforms. |
| Work-Life Balance | Does the company support remote work or flexible hours? | Example: Netflix allows flexible working days and locations. |
| Reputation and Company Type | Is the company a startup, large corporation, or niche firm? | Example: FAANG companies like Google or Big 4 consulting firms like Deloitte add significant value to your resume. |
| Industry Fit | Does the company operate in an industry you’re passionate about? | Example: Gaming companies like Ubisoft or EA. |
| Location | Is the company remote-friendly, or does its location impact your daily routine? | Example: Working in San Francisco offers networking opportunities but comes with higher living costs. |
Industries and Top Companies
| Industry | Top Companies |
|---|---|
| Info Tech | Apple, Microsoft, Google, Meta, Amazon, Nvidia, Salesforce, IBM, Cisco, ServiceNow, Intel, AMD, Broadcom, HPE, Adobe, MSI, Dell. |
| Healthcare | UnitedHealth Group, Johnson & Johnson, Pfizer, Abbott, Merck, Lilly, Medtronic, Abbvie, Amgen, Boston Scientific, Danaher, GE Healthcare. |
| Finance | JPMorgan Chase, Berkshire Hathaway, Mastercard, Visa, Wells Fargo, Citibank, BlackRock, Goldman Sachs, Aon, Morgan Stanley, American Express, Paypal. |
| Consumer | Walmart, Nike, Amazon, The Home Depot, Procter & Gamble (P&G), PepsiCo, Coca-Cola, eBay, TJX, Nestle, Costco, Target, IKEA. |
| Industrial | UPS, Honeywell, General Electric (GE), Boeing, Lockheed Martin, Caterpillar, Raytheon Technologies, Siemens, 3M, ABB, Eaton. |
| Communication | Google, Meta, Netflix, AT&T, Verizon, Comcast, T-Mobile, Walt Disney, Qualcomm, Cisco, Zoom, Twitter, Slack. |
| Energy | Exxon Mobil, Chevron, NextEra Energy, Duke Energy, BP, Shell, TotalEnergies, Phillips 66, ConocoPhillips, Schlumberger. |
| Gaming | Ubisoft, Electronic Arts (EA), Activision Blizzard, Nintendo, Epic Games, Valve, Square Enix, Zynga, Riot Games, Bethesda. |
| Automotive | Tesla, Ford, General Motors, Toyota, Honda, BMW, Mercedes-Benz, Volkswagen, Audi, Nissan, Rivian, Lucid Motors. |
| Retail/E-commerce | Amazon, Walmart, Alibaba, eBay, Target, Flipkart, Etsy, Shopify, JD.com, Rakuten. |
| Biotechnology | Moderna, Gilead Sciences, Illumina, BioNTech, Regeneron, Biogen, Genentech, Amgen, Vertex Pharmaceuticals, CRISPR Therapeutics. |
| Logistics/Shipping | FedEx, UPS, DHL, Maersk, XPO Logistics, J.B. Hunt, Cosco, SF Express, Ryder, Nippon Express. |
| Aerospace | Boeing, Airbus, SpaceX, Lockheed Martin, Raytheon, Northrop Grumman, Blue Origin, Virgin Galactic, Honeywell Aerospace. |
| Telecommunications | AT&T, Verizon, Vodafone, T-Mobile, Comcast, Orange, Deutsche Telekom, Telefónica, China Mobile, Singtel. |
| Food & Beverage | PepsiCo, Coca-Cola, Nestle, Mondelez, McDonald’s, Starbucks, Yum! Brands, Tyson Foods, Kraft Heinz, Danone. |
| Entertainment | Netflix, Walt Disney, Warner Bros. Discovery, Sony Pictures, Universal Pictures, Paramount, Lionsgate, Spotify. |
| Pharmaceuticals | Pfizer, Johnson & Johnson, Novartis, Roche, GSK, AstraZeneca, Sanofi, Merck, Abbvie, Takeda Pharmaceuticals. |
| Energy/Renewable | NextEra Energy, First Solar, Vestas Wind Systems, Siemens Gamesa, Sunrun, Tesla Energy, Brookfield Renewable, Iberdrola, Enphase Energy. |
6. What should I know before switching jobs in cybersecurity?
How to Use the Above Table:

- Identify the industries you’re passionate about or align with your skills.
- Research the companies in your desired industry using tools like LinkedIn, Glassdoor, and company websites.
- Use this as a reference to create a company comparison spreadsheet in Excel or Notion, tracking factors like revenue, reviews, and future opportunities.
Steps to Research Effectively

- List industries and companies that interest you.
- Use LinkedIn, Glassdoor, and company websites to gather insights.
- Create a spreadsheet to track revenue, employee reviews, culture, and industry focus.
- Prioritize the 2–3 factors most important to you (e.g., compensation, career growth, flexibility).
- Regularly update your research as companies evolve.
7. How do I find a quality mentor who truly adds value?
Finding the right mentor is challenging, especially for beginners in the security field. Use this table to explore the DOs and DON’Ts before selecting your mentor:
DOs  | DON’Ts  |
|---|---|
| Select a mentor who is down to earth, willing to learn and coach. | Don’t select mentors solely based on their number of certifications. |
| Look for mentors who provide a clear vision and guidance for your career goals over 2–5 years. | Don’t base your decision only on their online presence or popularity. |
| Choose mentors who contribute to the community regularly. | Avoid choosing mentors just for their technical hacking skills. |
| Select a mentor with specific expertise in your area of interest. | Don’t select mentors only for their number of years of experience. |
| Ensure they are reasonably available and communicative for guidance. | Avoid those who are unresponsive or overly busy. |
| Choose mentors with the right attitude alongside technical knowledge. | Don’t focus solely on their achievements or fame. |
| Give time to research and regularly communicate with potential mentors. | Don’t rush the decision without proper evaluation. |
| Select more than one mentor with diverse mentorship styles to maximize benefits. | Don’t expect one mentor to meet all your learning needs. |
| Look for mentors who can connect you to other professionals and resources. | Don’t skip evaluating how well their mentorship style aligns with you. |
| Choose mentors who inspire and motivate with their passion for the field. | Don’t settle for mentors who don’t show enthusiasm or willingness to guide. |
| Find mentors who are patient, understanding, and provide constructive feedback for growth. | Avoid mentors who overwhelm or discourage you. |
Additional Tips for Selecting a Mentor
- Research Thoroughly: Talk to potential mentors regularly and understand their approach before committing.
- Discuss Availability: Ensure the mentor is available for weekly or monthly check-ins. Clarify the preferred communication mode (e.g., in-person or online).
- Focus on Patience and Feedback: A good mentor should provide constructive feedback without making you feel overwhelmed.
- Look for Inspiration: The best mentors are those who inspire and motivate you with their passion for the field.
Final Thought: While no mentor will check every single box, prioritize the ones who align most with your needs. Remember, mentorship is a two-way street—commit to learning and contributing to make the relationship successful.
8. What factors should I consider before applying for a job?
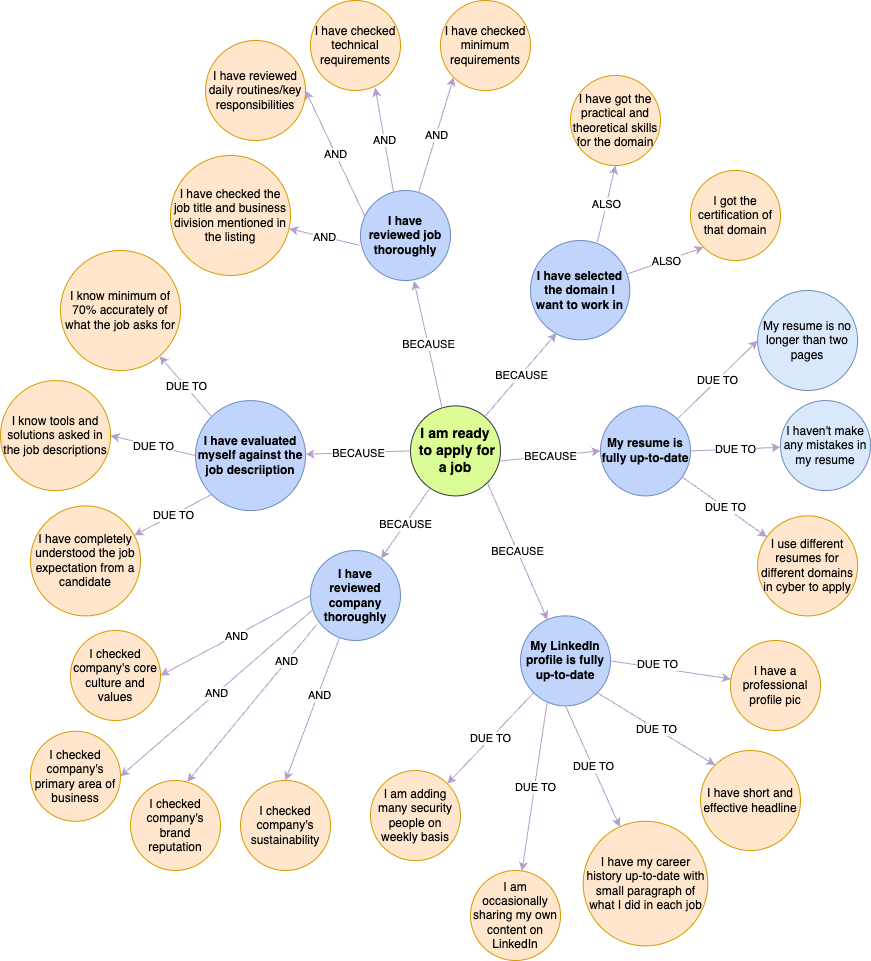
Proven Job-Hunting Tips for Cybersecurity Careers
General Tips
Experienced IT Professionals:
Tailor your resume to reflect cybersecurity skills rather than just general IT experience. Highlight relevant projects or certifications.
TIP: Use cybersecurity-specific resume templates available online.Beginners:
Create a professional resume even if you lack work experience. Focus on showcasing your technical skills, certifications, and learning progress.
No Professional Experience?
Add the following to your resume:- Certifications (e.g., CompTIA Security+, CEH).
- Labs or practical projects (e.g., TryHackMe, Hack The Box).
- Volunteer work or participation in cybersecurity-related community events.
Where to Apply
Use multiple job portals but don’t forget Google Jobs.
WARNING: Many jobs listed on Google Jobs are not available on LinkedIn or other platforms, so always check there.
These agencies often fill roles for big companies and are familiar with the industry demands.Connect with HR professionals in cybersecurity on LinkedIn.
Build relationships and ask them to review your profile for opportunities.
Interview Preparation
Prepare for interviews based on job descriptions (JD). Most questions will stem from the roles and responsibilities mentioned in the JD. Follow these steps for effective preparation:

- Understand the JD: Break down each line of the job description.
- Use ChatGPT or other AI modules:
- Give ChatGPT a paragraph summarizing the JD and company.
- Ask it to generate potential technical and scenario-based questions that may be asked during your interview.
- Practice Answers: Prepare answers to the questions and ensure you understand them practically, not just theoretically.
- Hands-On Practice: Find online labs/resources to learn practical skills if you are applying for technical security roles.
Example: Platforms like TryHackMe or Hack The Box. - Soft-Skill Questions: Evaluate what behavioral or soft-skill questions may be asked. Prepare specific examples to showcase your problem-solving and teamwork skills.
- Mock Interviews: Conduct mock interviews to boost your confidence.
9. What should I focus on after landing my first cybersecurity job?
Congratulations! 🎉 But Mission NOT Completed.
Landing your first job is a significant achievement, but it’s just the beginning. Here’s everything you need to focus on to thrive and grow in the dynamic field of cybersecurity.
1. Continue Learning
- Focus on skills you can only learn in your company, not through Google or YouTube. - *Example*: Designing secure architecture diagrams for DevSecOps projects tailored to your company’s infrastructure. - Real-world experience is invaluable—seek hands-on projects that challenge you and build expertise.2. Plan for Career Advancement
- To move to management roles, focus on learning: - Soft skills in business and leadership. - Problem-solving strategies involving **people, processes, and technology**. - Broaden your understanding beyond technical knowledge to prepare for leadership responsibilities.3. Know Your Competition
- Use competition as motivation to push yourself further. - Stay connected with your network and observe what others are learning and achieving. - Use their progress to inspire your own growth while maintaining a collaborative mindset.4. Understand the Cybersecurity Market
- Track industry trends and new vendors launching innovative solutions. - Follow podcasts, conference discussions, and online panels to understand: - Current challenges in the cybersecurity landscape. - Future roles and skills that will be in demand. - Compare how the market looked when you started your career versus where it’s heading. Set goals based on these insights.5. Stay Positive and Motivated
- In cybersecurity, you’ll encounter people who know more than you—it’s part of the learning process. - *Mindset*: “If they know 2 things and I know 1, I can now learn and make it 2 for both of us.” - Stay focused on your growth instead of comparing yourself negatively.6. Use the Right Tools
- Make **StackOverflow, ChatGPT, and Google** your best friends. - It’s not about knowing everything but being able to learn quickly and effectively. - Don’t hesitate to ask questions—even if they feel “stupid.”7. Build Community Presence
- Attend local meetups and present topics you’re familiar with to build public speaking confidence. - Gradually progress to national and international conferences. - Networking with professionals at events can open doors to mentorship and career opportunities.8. Avoid Bad Practices in Cybersecurity
- Cybersecurity is not immune to bad practices, shortcuts, or unethical behavior. - Always validate your decisions and stay committed to integrity in your work.9. Work on Communication Skills
- Strong communication is essential in cybersecurity. Focus on: - Writing clear and professional emails. - Presenting projects effectively. - Engaging in impactful daily conversations. - Your ability to articulate ideas well can significantly enhance your career impact.10. Seek and Offer Mentorship
- **Find Mentors**: Seek experienced professionals to guide you and provide valuable advice. - **Be a Mentor**: Share your knowledge with newcomers to build your leadership skills and contribute to the community. - Mentorship is a two-way street, offering mutual growth and learning.11. Maintain Work-Life Balance
- Long-term success requires balance. Prioritize your mental health and personal life alongside your career. - Invest time in: - Exercise and physical health. - Hobbies and personal passions. - Relaxation and spending time with loved ones.12. Earn Professional Certifications
- Enhance your credibility and expertise with certifications such as: - **CompTIA Security+, CEH, CISSP**, and more. - Certifications show your commitment to the field and make you stand out to employers.10. What essential fundamentals should I master as a beginner?
For newcomers to cybersecurity, mastering the fundamentals can seem daunting due to the sheer number of areas to cover. Below is a categorized breakdown of areas, skills, and resources to guide you as you start your cybersecurity journey.
| Area | Technical Skills | Soft Skills | Sub-Domain | Learning Approach | Resources |
|---|---|---|---|---|---|
| Fundamental Concepts | Cybersecurity basics (CIA triad), threat modeling, risk assessments, cybersecurity frameworks (NIST, ISO 27001) | Critical thinking, communication skills | Information Security Management | Study key principles, frameworks, and attack models | Cybrary, OWASP |
| Computer Networks | Network protocols (TCP/IP, DNS), firewalls, routers, intrusion detection systems, secure network architecture | Business impact of networks, teamwork | Network Security, Secure Design | Get certifications like CCNA, Network+; Build hands-on labs | Cisco Academy, CompTIA |
| Cryptography | Encryption (symmetric/asymmetric), PKI, hash functions, digital signatures | Attention to detail, ethics | Encryption, PKI Management | Study cryptography principles, practice real-world encryption | Crypto101, Coursera Cryptography Course |
| Software Security | Secure coding, vulnerability assessment, static and dynamic analysis | Patience, communication | Penetration Testing, Secure DevOps | Participate in Capture The Flag (CTF) challenges, secure coding | OWASP WebGoat, Hack The Box |
| System Security | System hardening, patch management, endpoint protection | Prioritization, cost awareness | Endpoint Protection, Access Control | Virtual labs, system hardening exercises | Microsoft Learn, CompTIA Security+ |
| Cloud Security | Cloud technologies (AWS, Azure, GCP), container security, virtualization | Risk management, compliance negotiation | Cloud GRC, DevSecOps | Get certifications like AWS Security, Azure Security Engineer | AWS Training, Microsoft Learn |
| Incident Response | Digital forensics, remediation, incident detection | Crisis management, decisiveness | Disaster Recovery, Incident Management | Participate in incident response drills | SANS, EC-Council |
| Threat Intelligence | TTPs (tactics, techniques, procedures), threat analysis, understanding intelligence sources | Analytical thinking, situational awareness | Strategic Intelligence, Threat Analysis | Follow cybersecurity news, practice analyzing threat reports | MITRE ATT&CK, Threatpost |
| Data Security | Data lifecycle, encryption, privacy regulations (GDPR, CCPA) | Ethical considerations, business impact | Privacy Compliance, Data Governance | Learn privacy laws, explore tools like DLP | IAPP, Coursera - GDPR |
| Mobile Security | Mobile OS architecture, mobile application security | Diligence, risk management | Mobile Threat Defense | Test app vulnerabilities in controlled environments | OWASP Mobile, Mobile Security Framework |
| Social Engineering | Phishing, pretexting, baiting | Understanding human behavior, empathy | Social Engineering, Awareness | Awareness training, phishing simulations | KnowBe4, Social Engineer |
| Governance, Risk, Compliance | Cybersecurity policies, risk assessment methodologies | Strategic thinking, communication skills | Cybersecurity Governance, Risk | Study for certifications like CISM, CRISC | ISACA, IT Governance Blog |
| Penetration Testing | Vulnerability analysis, Metasploit, Burp Suite, Wireshark | Critical thinking, reporting | Network, Web, Mobile Pen Testing | Learn methodologies (OWASP, PTES), hands-on labs | Offensive Security, OWASP Testing Guide |
| Red Teaming | Threat emulation, social engineering, advanced intrusion testing | Adaptability, collaboration | APT Emulation, Adversary Simulation | Participate in exercises, earn certifications | Red Team Journal |
| SOC (Security Operations Center) | SIEM tools (Splunk, QRadar), intrusion detection | Analytical skills, communication | Threat Monitoring, Incident Response | Work in SOCs, get certifications like CySA+ | SANS SOC Training, Splunk Fundamentals |
Improvements and Additions
- Learning Approach: Emphasizes hands-on learning (labs, certifications, CTFs).
- Resources: Verified platforms for self-paced and guided learning.
- Soft Skills: Highlights the human aspect of cybersecurity, such as communication, critical thinking, and decision-making.
11. What are common entry-level roles and titles in cybersecurity?
| Role | Description | Key Responsibilities |
|---|---|---|
| Security Analyst (Responsible for maintaining the security of an organization’s data) | Security analysts are integral to constructing security measures across organizations to protect the company from attacks. They explore vulnerabilities and recommend security improvements. | - Work with stakeholders to analyze cybersecurity posture. - Compile reports on networks and document security issues. - Develop security plans with up-to-date tools and trends. |
| Security Engineer (Design, monitor, and maintain security systems to prevent cyberattacks) | Security engineers develop and implement security measures using threat and vulnerability data. They focus on preventing breaches through design and tools. | - Test and screen software security. - Monitor and update systems to prevent vulnerabilities. - Implement and identify critical security systems. |
| Incident Responder / Digital Forensics (Handles incidents while an attacker’s operation is still unfolding) | Responds to security breaches and investigates causes through digital forensics. They analyze evidence and help prevent future attacks. | - Create and adopt actionable response plans. - Analyze digital evidence and report findings. - Support incident response and remediation measures. |
| SOC Analyst (Tier 1) (Incident Responder) | Monitors security alerts and network activities in real time in a Security Operations Center. First point of contact for identifying and escalating threats. | - Detect unauthorized activities and intrusions. - Discover policy violations. - Record incidents in logs for escalation to higher tiers. |
| SOC Analyst (Tier 2) (Advanced Incident Response) | Conducts deeper analysis on cybersecurity alerts and threat trends. Proactively hunts adversaries and resolves complex alerts. | - Perform deeper analysis of attacks. - Hunt for adversaries proactively. - Create reports based on investigation findings. |
| SOC Analyst (Tier 3) (Threat Hunter) | Focuses on advanced threat hunting and creating new adversary detection methods, including malware analysis and attack simulations. | - Perform reverse engineering and malware analysis. - Develop advanced detection mechanisms. - Conduct adversary research and threat simulations. |
| Penetration Tester (Junior) | Simulates real-world attacks to test the strength of an organization’s security system. | - Conduct network and system penetration tests. - Document vulnerabilities and recommend fixes. - Use tools like Metasploit, Burp Suite, etc. |
| Compliance Analyst (Adheres to cybersecurity policies and regulations) | Ensures organizational security practices meet regulations and standards like GDPR, CCPA, or NIST. | - Audit systems and security processes for compliance. - Train staff on compliance issues. - Prepare reports on adherence to regulations. |
| Vulnerability Analyst | Evaluates system weaknesses by scanning and identifying vulnerabilities to ensure security resilience. | - Conduct vulnerability assessments using tools like Nessus. - Report on prioritized fixes for vulnerabilities. - Keep up with emerging threats. |
| Security Consultant | Provides advice to organizations to improve their cybersecurity posture. | - Assess security requirements and gaps. - Suggest solutions tailored to organizational needs. - Design secure architectures. |
| Threat Intelligence Analyst | Monitors and evaluates threat landscapes to proactively identify security risks. | - Track adversary behaviors using tools like MITRE ATT&CK. - Provide intelligence reports to key stakeholders. - Assess risks based on global cyber trends. |
12. Is a master’s degree worth it for a career in cybersecurity?
This section explores whether pursuing a master’s degree in cybersecurity is a worthwhile investment for your career. Let’s break it down into myths vs. realities, advantages & disadvantages, and key considerations before choosing a program.
Myths vs. Realities
Myth  | Reality  |
|---|---|
| A Master’s degree in cybersecurity is not required. | True but not 100%. It offers intermediate benefits such as enhanced networking, soft skills, and academic recognition. |
| A Master’s degree guarantees a higher salary or quick job. | Generally false, unless it’s from a prestigious university with excellent placement programs. |
| Masters teach only theoretical concepts, not practical knowledge. | Not true. It varies by university; many programs integrate corporate and research-based learning. |
| Better chances of job interviews with a Master’s degree. | Not always. Skills and experience often outweigh academic credentials. |
Advantages of a Master’s Degree
- Global Exposure: Provides the opportunity to study abroad, gaining local cybersecurity market insights.
- Improved Communication: Collaboration with peers sharpens presentation and teamwork skills.
- Projects and Research: Academic projects enable real-world problem-solving experience.
- Expanded Networking: Connect with professionals and professors from diverse backgrounds.
Disadvantages of a Master’s Degree
- Lack of Real-World Security Experience: Doesn’t fully prepare for corporate cybersecurity work.
- Time Investment: Requires 2–3 years that could be spent gaining industry experience.
- High Costs: Tuition fees can be substantial, especially in foreign countries.
- Post-Study Visa Challenges: Difficulty in securing work visas after graduation in many countries.
Key Considerations Before Choosing a Master’s Program
- Post-Study Visa Opportunities: Ensure there’s clarity on sponsorship and visa pathways.
- Course Content: Review syllabi for hands-on labs and real-world applications.
- University’s Rank: Global/national rankings and reputation in cybersecurity education.
- Industry Partnerships: Collaborations with security firms or government agencies.
- Internship Opportunities: Check if the program includes internships or co-op placements.
- Career Services: Assess how effective the university’s career support team is in securing jobs.
- Cost and Duration: Evaluate total costs and time required against potential ROI.
- Local Cybersecurity Market: Research job demand in the country where the degree is pursued.
Final Thought Whether a Master’s degree is worth it depends on your personal goals, financial situation, and current level of industry exposure. If time and resources allow, pursuing a degree from a reputed institution can enhance your career. However, practical skills and certifications can often serve as viable alternatives.
13. How do I find and make the most out of internships?
Factors to Consider
- Type of Company: Product-based, consulting, or Big4.
- Internship Requirements: Skills and eligibility.
- Roles and Responsibilities: Daily tasks and learning scope.
- Employer Expectations: Clear expectations of your role as an intern.
✅ DOs and ❌ DON’Ts
| ✅ DOs | ❌ DON’Ts |
|---|---|
| Understand the company type (consulting, product-based, etc.). | Avoid companies that only provide coaching without real-world projects. |
| Ask about job responsibilities, tasks, and routines. | Beware of companies relying on PR campaigns or awards to attract interns. |
| Evaluate the learning opportunities available during the internship. | Avoid startups with extremely small teams unless their work aligns with your goals. |
| Clarify expectations with the employer beforehand. | Don’t pick companies expecting interns to teach or train instead of gaining hands-on experience. |
| Talk to people who have interned there to get reviews. | Avoid selecting companies solely based on their reputation in press or magazines. |
| Start searching at least six months in advance. | |
| Conduct mock interviews (minimum 5) with mentors or career counselors. | |
| Research the company’s strengths, weaknesses, and expertise. |
Making the Most of It
- Engage actively with teams and professionals at the company.
- Keep a detailed record of the projects, tools, and skills you learn.
- Regularly seek and implement feedback from mentors or colleagues.
- Utilize company resources to expand your knowledge and expertise.
14. Which certifications are best for beginners in cybersecurity?
Key Considerations Before Choosing a Cybersecurity Certification
| Category | Details |
|---|---|
| Certification from Reputable Authorities | Ensure the certification is issued by well-known authorities in cybersecurity. |
| - Cybersecurity-specific authorities: ISC2, eLearnSecurity, Offensive Security, ISACA, EC-Council, CompTIA, CREST, SANS, GIAC, etc. | |
| - Vendor-specific authorities: Amazon (AWS), Google (GCP), Microsoft (Azure), Cisco, Checkpoint, etc. | |
| Market Demand for the Certification |  |
| Beginner vs Advanced Certification | Understand if you’re opting for a beginner-level cert in your domain or directly aiming for a management/high-level cert. Plan your starting point and endpoint. |
| Certification Variety |  |
| Purpose of the Certification | Reflect on whether you’re pursuing the certification for: |
| - Job-specific purposes: Be cautious about spending a significant amount without a job guarantee. | |
| - Knowledge acquisition: A certification should ideally enhance your understanding and practical skills. | |
| Future Relevance of the Certification | Evaluate the longevity of the certification: |
| - Declining value examples: CEH has seen a reduction in perceived value compared to OSCP, OSCE, GPEN, etc. | |
| - Consistent value examples: Certifications like CISSP and Security+ have retained their relevance over time. | |
| Alignment with Career Goals | Ensure the certification aligns with your career aspirations. |
| - It’s beneficial to obtain certificates in both technical and managerial areas of your cybersecurity domain. |
Examples of Certification Lifespans and Perceived Value
- Long-lasting Value:
- CISSP: Highly respected in managerial and technical cybersecurity roles.
- Security+: Recognized globally and consistently in demand.
- Reduced Value Over Time:
- CEH: Initially popular but overshadowed by OSCP, GPEN, and OSCE for practical penetration testing skills.
By keeping these considerations in mind, you can better evaluate which certification aligns with your career path and goals.
15. Which is better: consulting firms or product-based companies?
How many types of companies are there?
Which types of companies should you consider in the initial stages of your cybersecurity career?
| Legends | Consulting (Big4 & Other Large Firms) | Small Consulting Firms | Product-Based Firms | Security Vendor Firms |
|---|---|---|---|---|
| Size | Giants, thousands of employees | Small to medium enterprises | Small, medium, or large enterprises | Small, medium, or large enterprises |
| Reputation | Well-reputed worldwide | Reputed locally (region or state); less likely to be global giants | Reputable within countries or internationally | Well-reputed in the security space |
| Example | KPMG, Deloitte, EY, PwC, Accenture, etc. | Local security consulting firms | Google, Microsoft, Apple, Amazon, Tesla, Walmart | CrowdStrike, Qualys, Tenable, Rapid7, RSA, Checkpoint, etc. |
| Client-Base | Serves clients globally | Limited to their region or niche | Global customer base | Global or local depending on the company |
| Project Type | Variety of projects: technical to management in all cybersecurity domains | Limited to their expertise (specific areas of cybersecurity) | Securing products and infrastructure | Two roles: customer support for products OR engineering security |
| Learning Opportunity | Vast: exposure to consulting and technical areas; cross-border teams | Limited: more self-learning required | Immense: focused learning on specific infrastructure | Domain-specific opportunities based on their security products |
| Your Role | Jack of all trades | Limited expertise in specific domains | Jack of all trades in company-specific security | Specialist in security products |
| Salary | Competitive | Depends on company size and revenue | Competitive based on company size | Competitive based on expertise and company scale |
Latest Insights and Market Trends
| Company Type | Advantages | Challenges |
|---|---|---|
| Consulting Firms (Big4) | - Diverse exposure to various industries | - High-pressure environments with tight deadlines |
| - Opportunity to build a global network | - Often requires significant travel for client projects | |
| - Access to cutting-edge tools and frameworks | - May involve shifting between multiple projects and domains | |
| - Structured learning and growth paths | ||
| Small Consulting Firms | - Greater flexibility in roles and tasks | - Limited exposure to diverse industries |
| - Closer interactions with leadership | - Resources and learning opportunities may not match large firms | |
| - Opportunity to make a noticeable impact in smaller teams | ||
| Product-Based Companies | - In-depth exposure to securing large-scale infrastructure or products | - Roles can become repetitive over time |
| - Work closely with in-house teams for long-term projects | - Limited movement between domains within the organization | |
| - Opportunity to master specific domains | ||
| Security Vendor Firms | - Focused on cutting-edge security technologies | - Niche focus may limit career movement outside the vendor space |
| - Opportunity to work on innovative products like endpoint protection, cloud security, and threat intelligence tools | - Requires deep technical expertise in specific products or technologies |
Factors to Consider While Choosing

- Career Goals: Are you aiming for diverse exposure or niche expertise?
- Work-Life Balance: Product companies often provide better work-life balance compared to consulting.
- Learning Curve: Consulting firms offer faster growth but may not allow deep specialization.
- Future-Proofing: Consider which roles align with emerging trends like cloud security, AI-based security, and DevSecOps.
- Network Building: Big consulting firms can provide networking opportunities across industries, while product firms allow you to build domain-specific expertise.
Final Takeaway
Both consulting firms and product-based companies have their unique advantages and challenges. Choose based on your career aspirations, the skills you wish to develop, and the type of work-life balance you prioritize. Keep the latest market trends in mind to ensure your choice aligns with future opportunities in cybersecurity.
16. How do I write a resume that stands out?
Key Activities to Build a Strong Resume in Cybersecurity
Want to break into cybersecurity but lack experience? Here are some great resume-building activities that can help you stand out:
- Volunteer with a cybersecurity conference.
- Teach a cybersecurity class.
- Mentor a student.
- Join a cybersecurity working group.
- Contribute to an open-source project.
- Build a home lab.
- Start a blog.
- Guest on a podcast.
- Lead a study group.
- Start a cybersecurity meetup or club.
- Obtain basic certifications like CEH, Security+, or equivalent.
- Earn certifications like AWS, Azure, or GCP.
- Participate in bug bounty programs and find vulnerabilities.
- Discover zero-day exploits and earn a CVE ID.
Accomplishing the majority of these activities will provide strong content for your resume and interviews.
 | Explanation |
|---|---|
| Typos and Grammatical Errors | It’s crucial to proofread your resume before submitting it. Errors may suggest a lack of attention to detail or professionalism. |
| Providing Inaccurate Information | Whether it’s wrong dates or exaggerated qualifications, falsifying information is always a big no-no. |
| Using an Unprofessional Email Address | Your email address should be simple, professional, and easily identifiable. Avoid inappropriate or quirky handles. |
| Including Personal Information | Details like age, religion, marital status, etc., could lead to unconscious bias or legal issues. |
| Having an Objective That’s Not Related to the Job | If you include an objective, it should directly relate to the position you’re applying for. |
| One-size-fits-all Resumes | Tailor your resume to the job. Highlight relevant experiences and skills. |
| Overloading Your Resume | Keep it concise (1-2 pages). Too much text can overwhelm and hide key points. |
| Listing Responsibilities Instead of Achievements | Employers care more about your accomplishments than job duties. Highlight results and impacts. |
| Including Irrelevant Information | Avoid hobbies or experiences that don’t relate to the job. Focus on relevant qualifications. |
| Not Using Action Verbs | Use strong action verbs to begin bullet points (e.g., “Designed,” “Implemented,” “Led”). |
| Using Clichéd Buzzwords | Words like “synergy” or “team player” are overused. Be specific about skills and accomplishments. |
| Lack of Specifics | Vague statements don’t help. Quantify your accomplishments (e.g., “Increased efficiency by 25%”). |
| Poor Formatting | Stick to a clean, professional layout with standard fonts. Avoid unusual styles or colors. |
| Including References on Your Resume | Unless asked, don’t include references. “References available upon request” is unnecessary. |
| Outdated Information | Remove irrelevant or old details unless highly relevant. |
| Not Using Numbers | Quantify achievements to give a clearer picture of your impact (e.g., “Managed $1M budget”). |
| Using an Inappropriate Resume File Name | Ensure the file name is professional and clear (e.g., “John_Doe_Resume.pdf”). |
| Having an Unfocused Career Objective or Summary | Clearly communicate your career goals and why you’re a fit for the position. |
| Excessive Jargon or Acronyms | Avoid too much technical jargon unless it’s industry standard. Explain acronyms if needed. |
| Inconsistent Tense | Use past tense for previous jobs and present tense for your current job. |
| Long Paragraphs | Use bullet points to make information easier to read and digest. |
| No Clear Structure | Organize your resume with headers, consistent formatting, and bullet points. |
| Using “I” or “My” | Avoid personal pronouns. Focus on action statements and achievements. |
| Not Highlighting Promotions | Highlight promotions to showcase career progression and achievements. |
| Not Aligning Resume and LinkedIn Profile | Ensure consistency between your resume and LinkedIn. Present a unified career narrative. |
| Lack of Contact Information | Include professional email and phone number. Ensure your LinkedIn profile is linked. |
| Including a Picture | Unless required, avoid including a photo. It could lead to bias and isn’t necessary. |
| Not Including a Cover Letter | A well-crafted cover letter provides context and personality, enhancing your application. |
| Not Showcasing Transferable Skills | Highlight skills applicable to the new role, especially when switching industries or positions. |
| Irrelevant Job Experience | Focus on experience relevant to the job. Leave out unrelated positions unless they showcase skills. |
| Missing Keywords | Include keywords from the job description for ATS optimization. |
| Overusing Bold or Italic Text | Use emphasis sparingly to avoid clutter and maintain professionalism. |
| No Hyperlinks to Professional Online Profiles | Include links to LinkedIn, portfolios, or other professional online profiles. |
| Including High School Information | Leave out high school details unless you’re a recent graduate. Focus on higher education or experience. |
By avoiding common mistakes and actively building relevant skills and activities, you can craft a strong, impactful resume that stands out to recruiters.
17. Why should I invest time in building a LinkedIn profile?
| Category | Details |
|---|---|
| Profile Picture | Choose a professional photo. Your LinkedIn profile picture should reflect professionalism and seriousness towards the platform. Avoid casual or overly social photos. |
 | Share and like content relevant to your profession. Avoid random posts, jokes, politics, or unrelated debates. Focus on cybersecurity topics to show expertise and interest. |
 | Write clear and concise posts. Avoid controversial topics, hate speech, or irrelevant content. Post about unique topics in your field and ensure your tone is professional and neutral. |
 | Share unique insights within your domain. Avoid over-discussed topics unless you add a new perspective. Be neutral and clear, avoiding slang or unprofessional language. |
| Be Polite and Gentle | Maintain professionalism when connecting or responding to others. Greet new connections politely. Handle negative comments gracefully and choose your words carefully. |
| Contact Information | Keep your profile updated with current email, phone number, and other contact details. Highlight roles, awards, and achievements in each job experience. |
| Introduction Paragraph | Write a strong introduction summarizing who you are, your experience, and your career goals. Clearly outline your expertise and future aspirations. |
| Achievements | Share relevant achievements only. Highlight awards and certifications aligned with your career goals. Avoid unrelated personal accomplishments. |
| Profile Title | Create a compelling two-line title. This should leave a strong first impression and summarize your professional identity. |
| Upload Documents | Add media (images, documents) to your experience section. Visual content enhances your profile and acts as a portfolio alongside your resume. |
| Ask for Recommendations | Recommendations from past colleagues and managers carry significant weight. Reach out to them for genuine endorsements. |
Why These Elements Matter
1. Professionalism:: Your profile is often the first impression recruiters and professionals have of you. A professional photo, clear title, and well-written introduction help establish credibility.
2. Content Sharing: Sharing and liking relevant content demonstrates your engagement with your field. It shows that you are actively involved and knowledgeable.
3. Network Building: Being polite and approachable makes it easier to build a network of like-minded professionals. Use LinkedIn messages to connect genuinely without overdoing formality.
4.Enhanced Visibility:Adding media files, detailed achievements, and recommendations makes your profile more robust and appealing to potential employers.
5. Career Opportunities: An updated profile with relevant skills and achievements makes you more attractive to recruiters. Highlighting certifications and projects boosts your employability.
By following these guidelines, you can make your LinkedIn profile a powerful tool for career advancement.
18. Why is finding a job abroad so challenging for international candidates?

Do you know how much it would cost a company if they sponsor a candidate outside of their own country? (I am taking an example of UK as I have UK experience)
| Cost Item | Small Sponsor (£) | Medium/Large Sponsor (£) | Description |
|---|---|---|---|
| Sponsor Licence Application | 536 | 1,476 | Valid for 4 years |
| Certificate of Sponsorship | 199 | 199 | Per sponsored candidate |
| Immigration Skills Charge | 364 (Year 1) + 182/6m | 1,000 (Year 1) + 500/6m | Based on sponsorship duration |
| Visa Application Fee | 479–943 | 625–1,235 | Depends on job type and visa duration |
| Immigration Health Surcharge | 624/year | 624/year | Per year of sponsorship (e.g., £1,872 for 3 years) |
| Estimated Total (3 Years) | ~2,800 | ~7,800 | Including all mandatory fees |
If candidate is married then they ask companies to sponsor for both him/herself and partner which would double this cost.
Imagine if you are running your own firm in UK, and if you are flooded with plenty of resumes locally from UK, would you rather spend above amount to hire someone outside of UK? No right, hence these is the main reason along with some other factors like time duration, paper work, etc. due to which companies hesitate to sponsor.
Key Challenges
| Challenge | Details |
|---|---|
| Visa Issues | Companies may hesitate to sponsor work visas due to high costs, paperwork, and risks. Some governments impose strict immigration rules, making it harder for employers. |
| Local Experience | Employers often prefer candidates with local experience to ensure familiarity with industry practices, regulatory requirements, and cultural norms. |
| Cultural Differences | Language barriers, communication styles, and understanding of workplace customs can impact a candidate’s ability to fit into the work environment. |
| Networking | Lack of local professional networks makes it harder for international candidates to learn about job opportunities and establish connections. |
| Unique Skill Requirements | Some positions require niche expertise, and companies may opt to hire locally to avoid sponsorship complications. |
Visa Sponsorship Challenges for Companies (Example: UK Tier 2 Visa)
| Step | Details |
|---|---|
| Obtain a Sponsor License | Companies must get licensed by the Home Office, demonstrating they are genuine and capable of managing sponsorship duties. |
| Certificate of Sponsorship | Employers issue this document to the candidate as part of their visa application process. |
| Resident Labour Market Test | (Replaced by a points-based system) Employers must show that the job is suitable for international candidates and meets skill and salary requirements. |
| Ongoing Sponsorship Duties | Companies must monitor and report compliance with visa conditions. Any failure can lead to penalties or loss of their Sponsor License. |
Key Takeaways for Candidates
| Insight | Benefits |
|---|---|
| Daily Applications and Rejections | Out of every applications, expect least minimum interview opportunity. Perseverance is key, and rejections should not deter you. |
| LinkedIn Networking | Expanding your network increases your visibility and may lead to referrals or job recommendations in the future. |
| Skill Development | Daily or weekly learning enhances your expertise, making you more competitive in the global market. |
| Content Sharing on LinkedIn | Sharing valuable insights showcases your knowledge and attracts positive attention from professionals worldwide. |
| Time Expectations | Foreign job hunting may take over a year. However, you’ll build valuable connections, knowledge, and experience during this process. |
Final Tips
- Patience Is Key: Job hunting abroad is a long-term effort, and there’s no guaranteed timeline for success.
- Manage Expectations: Treat the process like daily chores—keep working consistently without high expectations to avoid disappointment.
- Focus on Building Skills and Connections: Even if a foreign job isn’t immediate, the process enhances your professional profile and prepares you for future opportunities.
19. What’s the best approach to kickstart foreign job hunting?
By following the below bulletproof framework with dedication, you are setting yourself up for success in breaking into cybersecurity or landing a foreign job.
Step 1: Read the Guide
- Carefully read the entire guide word by word to understand the comprehensive process and strategies. There is not only 1 or few sections which would land you a job. A combination of multiple sections from this guide only will help you in your job hunt.
Step 2: Domain Identification
- Choose 2-3 cybersecurity domains you are interested in exploring further.
- Revisit the guide and focus on gathering 10 key answers for each domain.
- Narrow down your interests to 1-2 domains that align with your goals.
Step 3: Plan Your Learning Path
- Select a learning path based on your personal, professional, and social commitments.
- Find relevant resources (online platforms, certifications, mentors) to enhance your skills.
- If unsure about resources, connect with a mentor or expert for guidance.
Step 4: Continuous Learning Sharing to Create Outreach on LinkedIn
- Dedicate daily or weekly time to learning.
- Action Items:
- Share your learning experiences and takeaways on LinkedIn for visibility and networking.
- Update your resume and LinkedIn profile with new skills and expertise every 2 weeks.
- Action Items:
Step 5: Create Minimum 10 Target Countries

| Region | Description |
|---|---|
| EMEA | Europe, Middle East, and Africa. Covers countries in these continents. |
| APAC | Asia-Pacific. Includes Asia and Oceania (e.g., China, India, Australia). |
| AMER | Americas. Covers North, Central, and South America. |
| LATAM | Latin America. Focuses on Central and South America, including the Caribbean. |
| ANZ | Australia and New Zealand. Often part of APAC but sometimes distinct. |
| MENA | Middle East and North Africa. Subset of EMEA. |
| CIS | Commonwealth of Independent States. Includes Russia and neighboring countries. |
Step 6: Expand Your Network

- Add 30/40 security professionals (at least at your same designation or above, I prefer anyone who is manager and above) daily from your target countries of any region you chose from above.
- Rotate to a new country every week.

Add 20 security recruiters daily from the same target countries.
Engage in meaningful conversations and discussions.
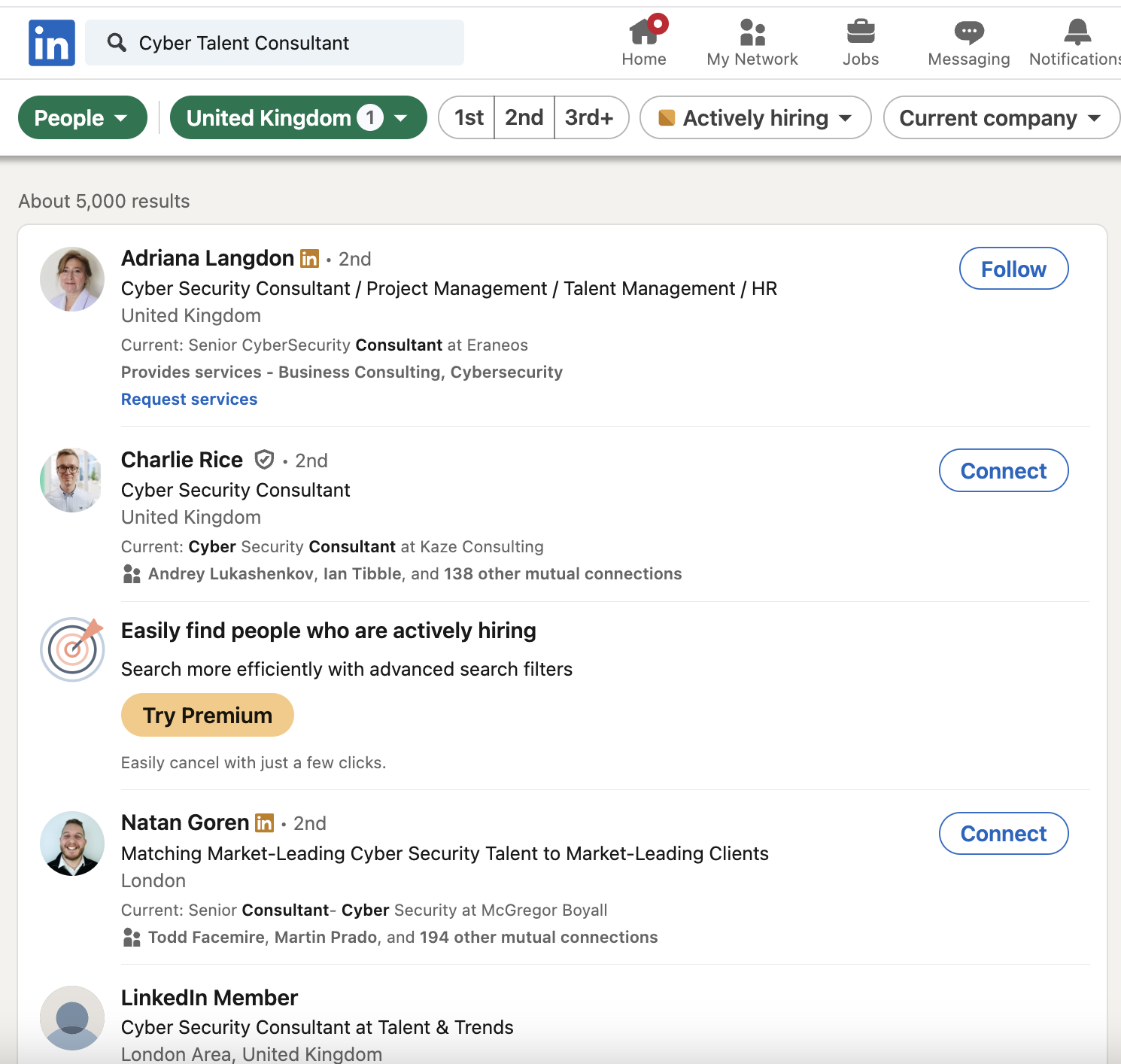
Below are the various roles for specific Cybersecurity Recruiters you can find on LinkedIn.
- Cybersecurity Recruiter
- Information Security Recruiter
- Cybersecurity Talent Acquisition
- Cybersecurity Headhunte
- Security Recruitment Specialist
- Cybersecurity Staffing
- Cyber Talent Consultant

Basic Search
(“Cybersecurity Recruiter” OR “Information Security Recruiter” OR “Cyber Talent Acquisition Specialist” OR “Security Recruitment Specialist”)
Targeting Specific Roles
((“Cybersecurity Recruiter” OR “Information Security Recruiter”) AND (“SOC Analyst” OR “Penetration Testing” OR “Cloud Security”))
Narrow by Location
((“Cybersecurity Recruiter” OR “Cyber Talent Consultant”) AND (“USA” OR “UK” OR “India”))
Targeting Agencies
((“Cybersecurity Recruiter” OR “Cybersecurity Staffing Specialist”) AND (“CyberSN” OR “Hays Technology” OR “Optiv”))

Step 7: Optimize Your Resume
Tailor your resume to match the job description:
- Identify important keywords from the job posting.
- Include these keywords strategically in your resume and LinkedIn profile.
Ensure your LinkedIn profile and resume reflect consistent and professional messaging.
Step 8: Apply Strategically
- Apply to 10 jobs daily in each target country.
- If focusing on your home country, follow the same routine.

Timeline and Expectations
- Duration: Follow this methodology consistently for 8 months to see tangible results.

- A cybersecurity job within a year.
- Expanded LinkedIn network and increased visibility.
- Valuable skills and knowledge.
Additional Benefits (Even Without Securing a Foreign Job)
- Expanded Network: Connect with professionals from diverse backgrounds and geographies.
- Regular Learning: Stay updated with the latest industry trends and insights.
- Enhanced Visibility: Gain recognition through LinkedIn activity and expertise sharing.
- Future Opportunities: Build relationships with connections who may help with referrals or recommendations.
Notes for Success
- Consistency is Key: Treat these steps as daily habits without expecting instant results.
- Mindset: Approach the process with patience and persistence, knowing that rejections are part of the journey.
- Networking Impact: Your connections and shared content can lead to unexpected opportunities over time.
20. How do I know it’s the right time to switch jobs?
21. What are the general DOs and DON’Ts in cybersecurity?
| ✅ DO | ❌ DON’T |
|---|---|
| Ask questions to yourself | Don’t waste money blindly |
| - Why this way? | - Do not go for paid courses that are already freely available on the internet. |
| - Why not that way? | Don’t get attracted by fame and money |
| - Am I getting investment vs return? | - Avoid fame and money games in the bug bounty industry. |
| - What is my investment (time, money, energy)? | Don’t apply shortcuts |
| - How much investment? | - Do not use shortcuts for certifications or job hunting. |
| - What should I expect out of this? | Don’t defame others |
| - What if I fail, any backup plan? | - Avoid defaming individuals or communities. |
| - Are there any alternatives or easier ways? | Don’t leak sensitive data |
| - How would I measure my success? | - Refrain from leaking or mishandling copyrighted or sensitive data. |
| - Who is my audience? Are my responses operational, technical, strategic, or social? | Don’t be an egotistic genius |
| - Avoid developing an ego or isolationist tendencies in your work. Stay collaborative. | |
| Develop curiosity | |
| - Keep asking, learning, and reflecting. Curiosity is the pathway to mastering cybersecurity. | |
| Work on a two-year target | |
| - Regularly evaluate where you see yourself every two years. | |
| - Share knowledge and learn from feedback to improve. | |
| Gain diverse exposure | |
| - Explore different areas of cybersecurity to become versatile and adaptable. | |
| Respect diversity | |
| - Treat all individuals equally, regardless of gender or background. | |
| Build healthy relationships | |
| - Maintain respectful relationships within the small, interconnected cybersecurity community. | |
| Avoid negativity in your content | |
| - Be neutral and constructive in your online and professional discussions. | |
| Engage with humility | |
| - Avoid using slang or aggressive language when interacting with peers or professionals. |
22. What challenges should beginners expect in cybersecurity?
| Area | Challenges | Solution |
|---|---|---|
| Communication Fear | - Don’t understand how to communicate with new professionals in the market. - Don’t understand business/corporate vs friendly/social communication. - Don’t know how to start talking with new professionals. - Don’t know what to talk about to build healthy relationships. | - Watch videos on professional communication skills. - Learn business and LinkedIn communication. - Practice structured communication with keywords from videos. - Focus on building professional relationships. |
| Unprofessional Communication | - Asking directly for jobs or references. - Asking Googleable questions. - Chasing people excessively. - Writing long, unclear emails. - Sending resumes without being asked. - Ignoring tone in messages. | - Keep communication concise and professional. - Start with simple interactions. - Build healthy relations over time. - Observe professional communication styles and adapt. - Avoid oversharing or pestering. |
| Lack of Patience | - Beginners often lack patience and expect instant responses. - Frequently chase HR or others for replies, calls, or updates. | - Allow sufficient time for responses. - Understand your priorities may not be theirs. - Explore alternatives for unanswered needs. - Be consistent without appearing desperate. |
| Writing Blunders | - Many mistakes in resumes, LinkedIn profiles, and emails. - Poor structure and tone in communication. - Overloading irrelevant information or failing to emphasize strengths. | - Follow professional templates for resumes and LinkedIn. - Proofread all written communication. - Use clear and concise formatting. - Highlight only relevant achievements and skills. |
| Lack of Industry Understanding | - Assumptions about how companies work vs reality. - Misunderstanding bug reporting processes or professional workflows. - Unrealistic expectations from HR regarding response times. | - Understand internal company workflows. - Seek mentorship or guidance. - Maintain realistic expectations for communication timelines. - Avoid making assumptions and seek clarification when needed. |
| Poor Grades | - Hesitant to show grades on resumes due to low performance. - Concerned about how grades affect opportunities. | - Focus on showcasing skills and practical knowledge. - Be transparent about grades if asked and provide context. - Highlight certifications or ongoing learning initiatives. - Prioritize technical and hands-on skills in resumes. |
| Lack of Self-Learning | - Over-reliance on others for easily accessible answers. - Not utilizing available resources like YouTube or Google effectively. | - Use YouTube and Reddit for tutorials and problem-solving. - Develop self-research habits. - Ask only when information is unavailable online. - Build a practice routine for independent learning. |
| Unsure Which Companies to Target | - Uncertainty about whether to apply to product-based, consulting, or security-specific firms. - Lack of understanding about market opportunities. | - Research the pros and cons of each company type. - Match your skills to company needs. - Narrow down preferences based on career goals. - Seek mentorship for guidance on which companies suit your interests and expertise. |
| Demotivation | - Feeling unmotivated due to lack of knowledge or experience. - Comparing oneself unfavorably to others in the industry. | - Identify knowledge gaps and address them systematically. - Focus on achievable short-term goals. - Celebrate small wins and milestones. - Seek community or peer support for encouragement and guidance. |
Additional Notes:
- Patience and Perseverance: Career growth in cybersecurity takes time and effort. Build skills steadily and avoid expecting instant success.
- Networking is Key: Strong professional networks can help overcome many challenges.
23. How do I stay up-to-date with cybersecurity trends?
Actionable Methods to Stay Updated

| Method | Description | Action Steps |
|---|---|---|
| Subscribe to Newsletters | Many cybersecurity organizations and blogs share regular updates through newsletters. | - Subscribe to sources like Krebs on Security, Dark Reading. |
| Join Cybersecurity Communities | Engage with peers in forums, Slack groups, and Discord channels. | - Join communities like Reddit’s r/cybersecurity, OWASP Slack, or Threat Intelligence Discords. |
| Participate in Webinars and Conferences | Attend virtual and in-person cybersecurity conferences to gain insights from industry leaders. | - Follow events like Black Hat, DEF CON, or local InfoSec meetups. - Watch recordings or join live sessions. |
| Utilize RSS Feeds | Aggregates content from various cybersecurity blogs and news outlets in one place. | - Use RSS readers like Feedly or Inoreader to follow blogs like SANS, ThreatPost, and BleepingComputer. |
| Take Online Courses | Regularly update your skills by learning new methodologies, tools, or frameworks. | - Enroll in platforms like Cybrary, TryHackMe, Hack The Box, or Udemy. |
| Read Research Papers and Whitepapers | Stay informed about emerging threats and security techniques through research from credible sources. | - Follow sources like IEEE Xplore, Usenix, or arXiv for relevant papers. |
| Follow Thought Leaders | Stay connected with cybersecurity influencers who regularly share insights and updates. | - Follow professionals like Bruce Schneier, Troy Hunt, and organizations like CISA, NIST, and EFF. |
| Monitor Cybersecurity Blogs and Sites | Regular reading of specialized blogs can help identify trends. | - Read blogs like The Hacker News, CSO Online, and Rapid7. |
| Subscribe to Threat Feeds | Continuous threat intelligence updates from security companies. | - Use platforms like AlienVault OTX, IBM X-Force Exchange, or Cisco Talos. |
| Set Alerts and Automation | Use Google Alerts or automation tools to get updates on specific cybersecurity topics. | - Create alerts for keywords like “cyber attack”, “zero-day vulnerability”, or “data breach”. |
| Participate in Capture the Flag (CTF) | Helps in practical learning of current cybersecurity techniques and tools. | - Participate in events hosted by platforms like PicoCTF, Hack The Box, or local universities. |
DOs and DON’Ts of Staying Up-to-Date
| ✅ DO | ❌ DON’T |
|---|---|
| - Know your domain focus (e.g., SOC, Pentest, Cloud Security). | - Don’t add irrelevant hashtags or follow unrelated trends. |
| - Use hashtags to filter specific content (latest 24 hours/week). | - Don’t waste time on overly broad hashtags or outdated trends. |
| - Create a schedule for regular updates and research. | - Don’t consume random content without verifying its credibility. |
| - Take notes and create summaries for key learnings. | - Don’t blindly share or rely on unverified information from social media. |
| - Engage with communities for discussions and shared insights. | - Don’t ignore critical feedback or constructive suggestions in community discussions. |
| - Bookmark useful resources and categorize them for easy reference. | - Don’t overload yourself with excessive resources; focus on quality over quantity. |
By implementing these strategies, you can stay ahead in the rapidly evolving cybersecurity landscape.
24. Why can’t I become a CEO right out of my degree?

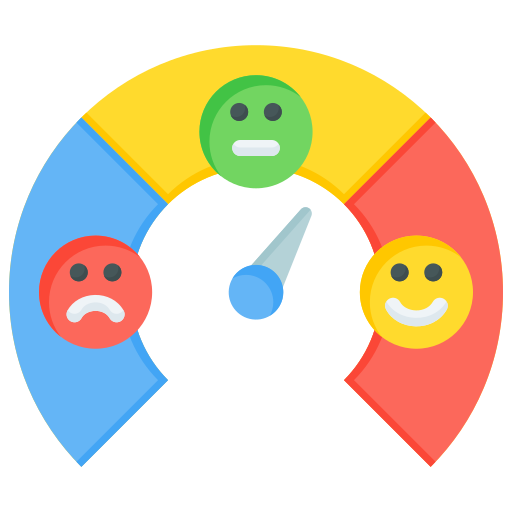
No Market Experience

No Competitor Experience

No Professional Experience with Customers

No One Knows or Trusts You

Struggle to Get Projects

Long Gap in Professional Experience
Lose Patience

Reputation at Stake When Searching for a Job
How to Succeed as a CEO in the Market
Core Elements for Success

| Solid Product | Unique Service | Solid Funding |
|---|---|---|
| Creating a product that is unique and solves significant problems for enterprises. Ensure no other product in the market is as good as yours, and include all features to meet any large enterprise’s needs. | Offering no common services (like code reviews or standard risk management assessments). Instead, provide services that are unique and deliver exceptional value compared to competitors. | If you don’t have a great idea, invest in building an exceptional service or product with the help of a skilled and experienced team. |
| A strong product stems from a thorough understanding of industry gaps and an innovative approach to address them. | Differentiate by creating unmatched value. Ensure superior quality and unmatched customer service. | Invest in experienced BDMs (Business Development Managers) to establish strong client connections and secure projects for your company. |
Without any of the above, there is no way to survive in the market. This is guaranteed.
Approach to Creating a Solid Product
Conduct a Literature Review: Study existing products and services to identify what has been done before.
Perform a Market Review: Understand industry gaps and customer pain points.
Assess Market Gaps: Determine whether your product can fulfill unmet needs in the industry.
Evaluate Feasibility: Analyze whether the product idea is viable in terms of resources, time, and potential success.
Calculate Costs and Efforts: Determine the time, money, and operational efforts required to build and sustain the product.
Project Success Timelines: Understand how long it will take to market and generate revenue.
Identify Your Target Industry and Country: Focus your efforts on industries and countries that are most likely to adopt your product.
Iterate on Your Idea: Consider every factor before starting, as these are essential steps to ensure your success.
Post-analysis, create your product and sell it in the market as a dynamic entrepreneur. With thorough preparation and analysis, you can position yourself for success in a highly competitive and fast-paced market. Take your time, conduct proper research, and avoid rushing into decisions that might compromise your vision.
25. How do I stay motivated and overcome setbacks?
Demotivation in cybersecurity is not new. With the high level of competition in the industry, common causes include:
- Observing others’ success while feeling stuck.
- Facing disrespect or indifference from peers or employers.
- Struggling to find a clear path to success.
- Falling prey to the allure of fame and monetary rewards on social media.
- Any other personal challenges or setbacks.
What You Need to Realize
The key to staying motivated in cybersecurity lies in shifting your perspective about learning and growth. Here’s the approach to take:
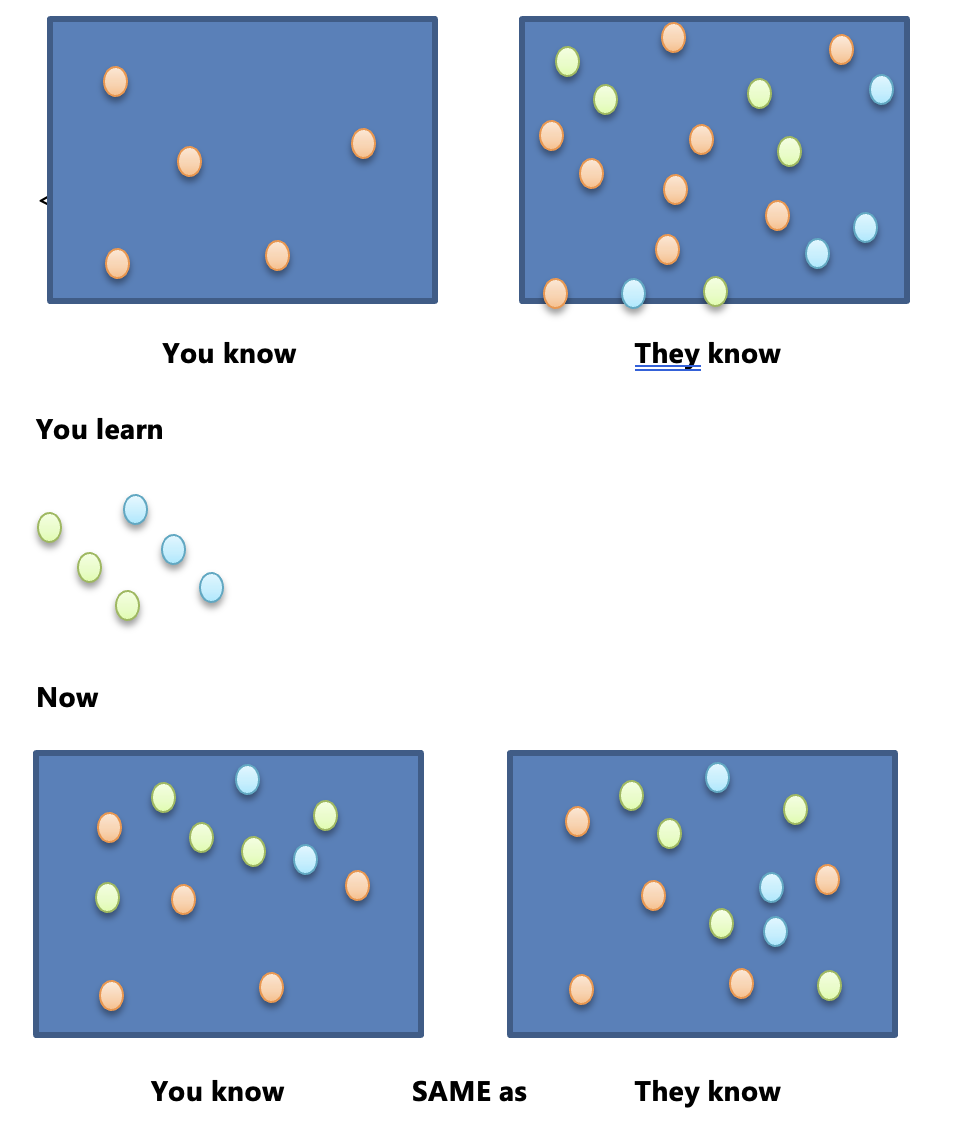
Accept the Knowledge Gap
Others may seem to know more than you, but remember, it’s all about expanding your own knowledge. Identify what they know that you don’t.Leverage Resources
- Learn from YouTube, blogs, and free materials.
- Find mentors who can guide you in the right direction.
- Focus on understanding what skills you lack and work on them.
Celebrate Learning Progress
Every time you gain new skills or knowledge, you’re narrowing the gap between what you know and what they know. This should motivate you to keep going.Adopt a Growth Mindset
Instead of seeing others’ success as discouraging, view it as inspiration. If someone knows five things you don’t, use that as an opportunity to learn and grow.Be Grateful for Guidance
Appreciate the people or resources that help you learn. Without them, you might not have realized what you needed to grow.Document and Reflect
Keep a note of what you’ve learned. Revisit this regularly to track your progress and stay motivated.
Overcoming Demotivation Due to Experience Gap
It’s common to feel intimidated or demotivated when comparing your experience to those who have been in cybersecurity for decades. However, here’s a fresh perspective to help you stay motivated:
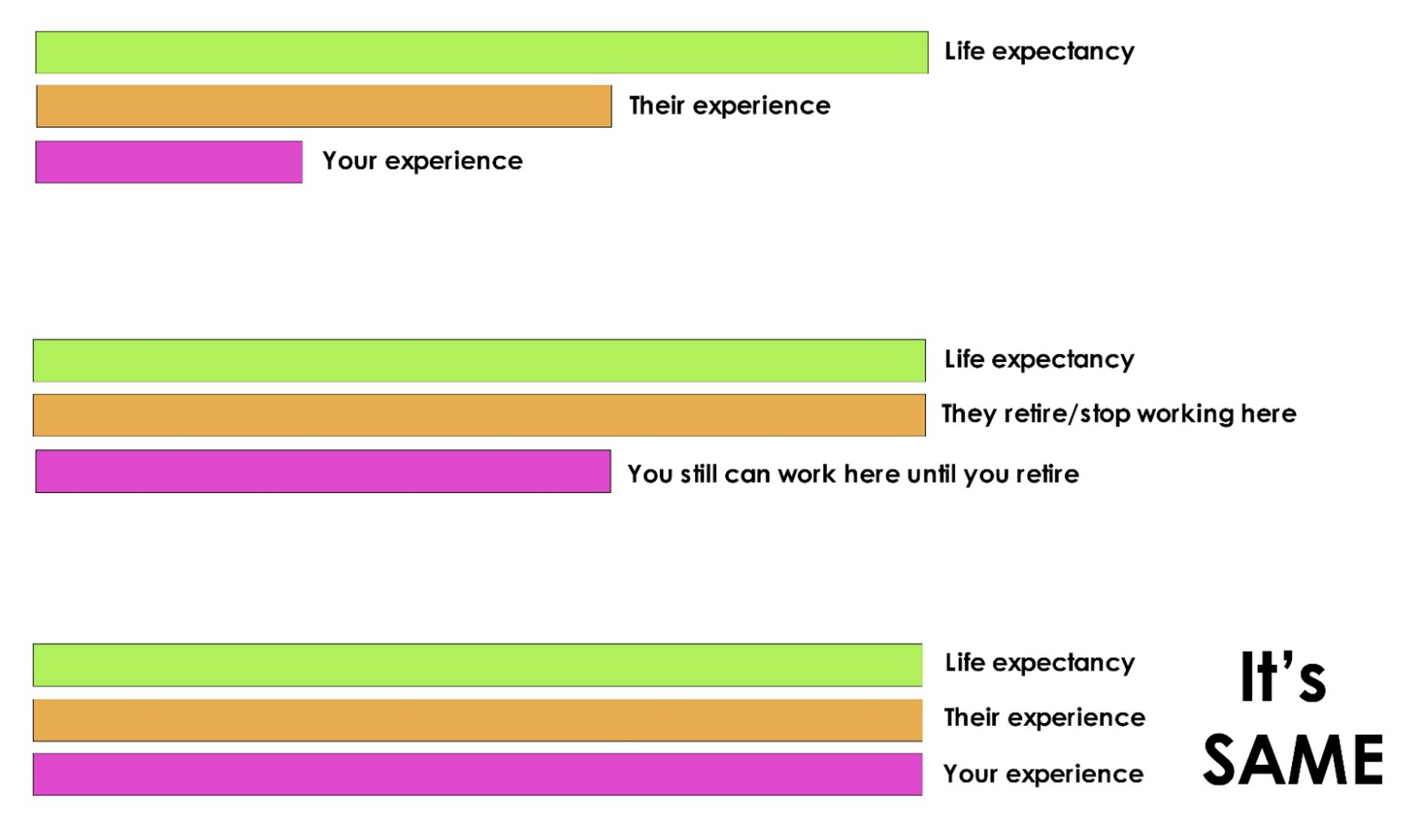
The Reality of Experience
Experience vs. Life Expectancy
While others may have more experience today (orange bar), you still have time (pink bar) to build your own expertise. Everyone starts somewhere.Time Is on Your Side
Over time, experienced professionals will retire or step away from the field. By then, you’ll be in a position to fill their shoes with your accumulated experience.A Future Edge
Younger professionals (pink bar) often have the advantage of learning and adapting to newer technologies. This positions you for a more dynamic career in the future.
26. Why not to start career with only Bug-Bounty?
Read this blog - https://chintangurjar.com/posts/full-time-bug-bounty/
The Final Perspective
By constantly learning and growing, you can bridge the knowledge gap. If someone knows more today, it’s an opportunity for you to catch up tomorrow. With dedication and focus, you’ll be able to stand on equal ground in terms of skills and expertise.
At the end of the day, we all have the same life expectancy to grow and learn. The journey is about making the most of the time you have, staying adaptable, and advancing with the evolving landscape of cybersecurity.
Embrace your potential, keep learning, stay positive, and remember that your career is a marathon, not a sprint.
DISCLAIMER
This guide has been written pre-ChatGPT era. However since we have GPT now I have used it to enhance the guide but its not completely written by GPT only. All of the information collection, organization, and presentation are my own thoughts.