Introduction
In today’s cloud-native world, APIs are the backbone of digital ecosystems connecting microservices, external partners, and end-users alike. But with increased connectivity comes a growing attack surface. Securing APIs isn’t just about protecting endpoints; it’s about embedding security across the entire API lifecycle. From planning and design to runtime enforcement and telemetry, modern API protection requires a layered, identity-driven approach. This article presents a visual and conceptual framework for API security combining DevSecOps principles, NIST-guided controls, Zero Trust architecture, and gateway deployment best practices. Through diagrams and detailed breakdowns, we offer a holistic view of how to operationalize API security across your organization.
Part 1 - Visualizing the API Protection Framework: From Plan to Runtime
APIs have become the lingua franca of modern enterprise systems powering everything from microservices meshes to third-party integrations. With that ubiquity comes risk: how do we make sure every API call is planned, built, and monitored in a consistent, repeatable way? The API Protection Framework diagram below captures the full DevSecOps life-cycle of API security, showing how pre-runtime and runtime controls each split into basic vs. advanced levels work together to mitigate common API risks.
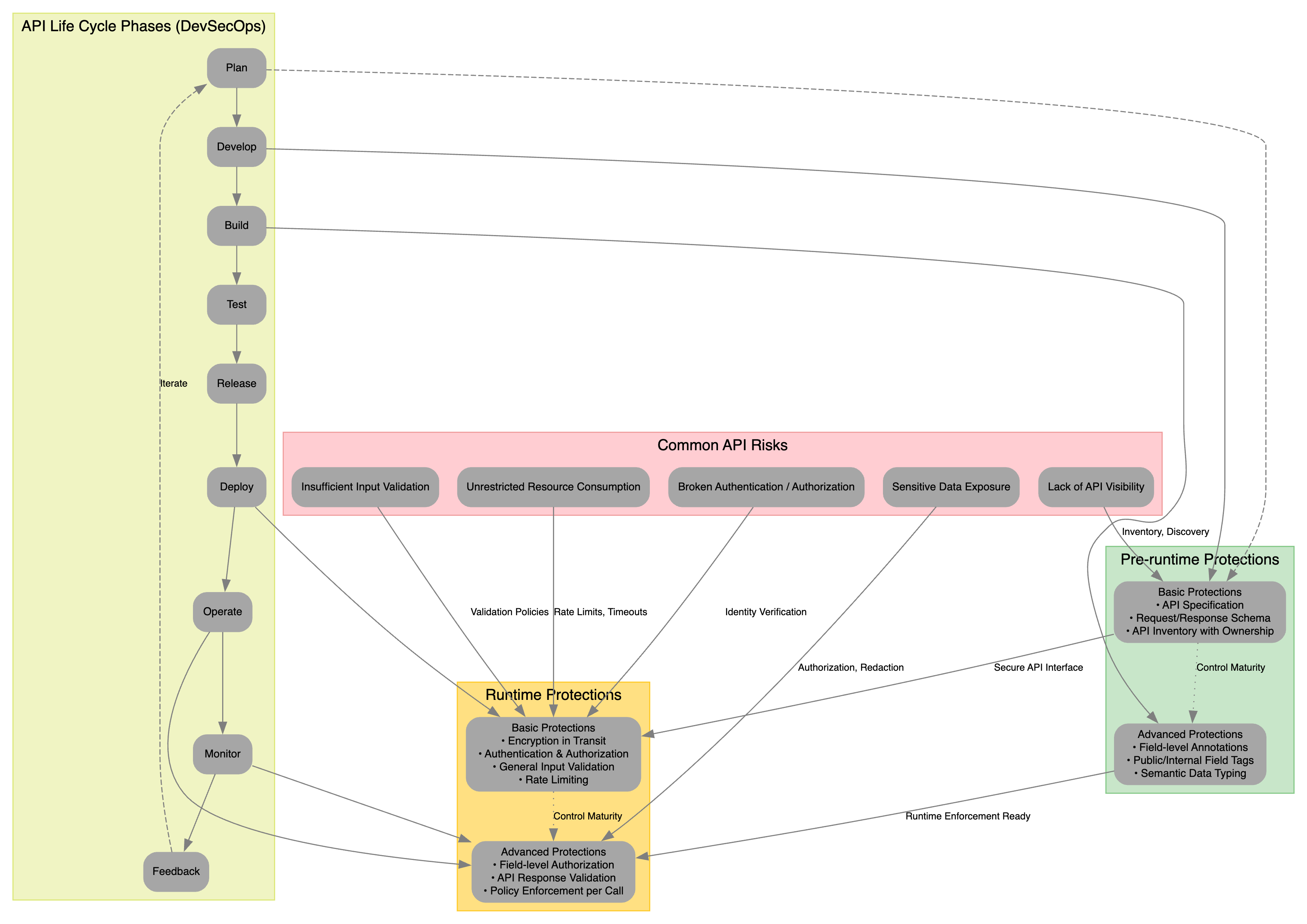
1. The DevSecOps API Life-Cycle
On the left side of the diagram, you’ll see the familiar DevSecOps loop:
Plan → Develop → Build → Test → Release → Deploy → Operate → Monitor → Feedback
Security (the “Sec” in DevSecOps) isn’t tacked on at the end it iterates alongside every phase. The diagram’s dashed arrows from Feedback back to Plan emphasize continual improvement: as new threats emerge, your team loops back to refine APIs and controls.
2. Mapping Common API Risks
At the heart of the framework is a call-out of the top Common API Risks:
- Insufficient Input Validation
- Unrestricted Resource Consumption
- Broken Authentication / Authorization
- Sensitive Data Exposure
- Lack of API Visibility
Each risk maps to both pre-runtime and runtime controls. By visualizing these connections, teams can see exactly where to apply which protection.
3. Pre-Runtime Protections
Pre-runtime controls are those you bake in before an API ever goes live during Plan, Develop, Build, Test, and Release. The green box on the right breaks these into:
3.1 Basic Pre-Runtime Protections
- API Specification
• Define every endpoint, request payload, and response schema (e.g. via OpenAPI, gRPC). - Request/Response Schema Validation
• Enforce field types, length limits, required vs. optional fields. - API Inventory & Ownership
• Maintain a living catalog of all APIs (internal & external) plus who owns them.
3.2 Advanced Pre-Runtime Protections
- Field-Level Annotations
• Tag each field aspublicvs.internalor with sensitivity labels (PII, PHI, PCI). - Semantic Data Typing
• Use domain-specific types (e.g.EmailAddress,Currency) to catch logic errors early. - Automated Policy Generation
• Generate fine-grained authorization rules from your API spec (e.g. per-field access control). - Control Maturity Metrics
• Track adoption levels across your estate (e.g. percentage of APIs with up-to-date specs).
4. Runtime Protections
Once an API is live in Deploy, Operate, Monitor, Feedback runtime protections guard every request/response cycle. The gold box in the center shows:
4.1 Basic Runtime Protections
- Encryption in Transit (TLS everywhere)
- Authentication & Authorization
• Verify both service identity (mTLS, SPIFFE) and end-user identity (OAuth2/OIDC). - General Input Validation
• Reject malformed requests at the gateway (e.g. oversized payloads, invalid JSON). - Rate Limiting & Timeouts
• Protect against DoS or runaway processes by imposing sensible defaults.
4.2 Advanced Runtime Protections
- Field-Level Authorization
• Enforce per-attribute access control based on user roles or service identity. - API Response Validation & Redaction
• Strip out any internal fields before sending data back to low-trust callers. - Policy Enforcement per Call
• Apply fine-grained policies (e.g. dynamic quotas, geo-restrictions) on each API invocation. - Runtime Enforcement Readiness
• Ensure your gateway, sidecars, or service mesh are configured to enforce these rules at wire-speed.
5. Bridging Pre- and Runtime
Notice how arrows flow between the green “Pre-runtime” and gold “Runtime” boxes this reflects Control Maturity. For example:
- A field tagged as internal in your spec (pre-runtime) can automatically be redacted by your gateway at runtime.
- Rate and size limits defined in your API doc feed directly into gateway policies.
- Ownership metadata in your API inventory maps to alerting & escalation flows during runtime incidents.
6. Continuous Feedback & Improvement
The diagram’s loop from Monitor→Feedback back to Plan reminds us that:
- Telemetry (logs, metrics, traces) must be collected for every protection.
- Incidents & anomalies drive refinements new risks may call for new spec attributes or upgraded enforcement capabilities.
- Control maturity should be measured over time, closing gaps in both pre-runtime and runtime protection levels.
Part 2 - API Risk and Control Matrix
The API Risk and Control Matrix provides a clear mapping between the most common API vulnerabilities and the mitigation controls both pre-runtime and runtime recommended by NIST. By aligning each risk to one or more security controls, teams can ensure that every threat vector is countered with appropriate defenses.
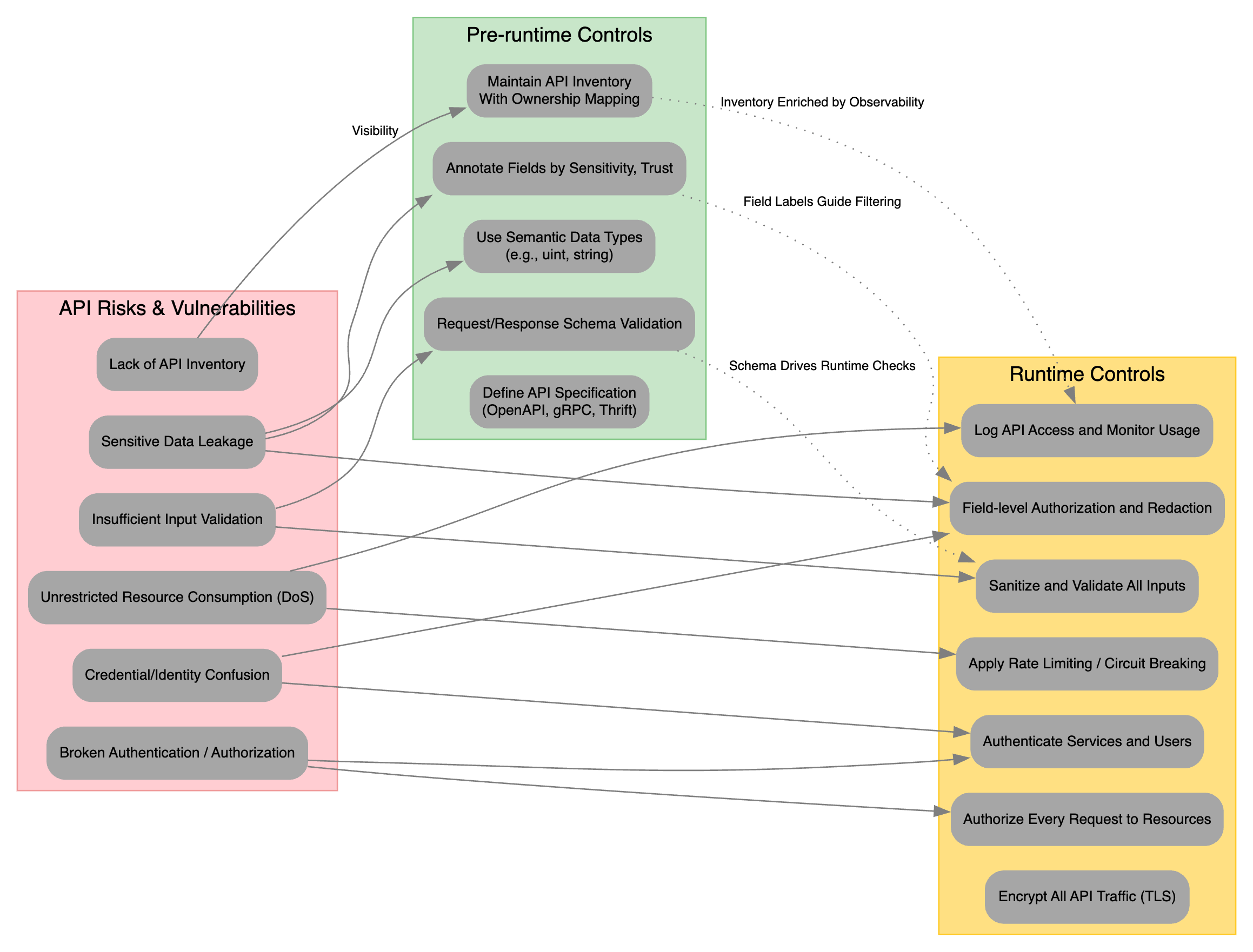
1. API Risks & Vulnerabilities
On the left, the matrix enumerates key API risks and vulnerabilities:
- Lack of API Inventory
- Sensitive Data Leakage
- Insufficient Input Validation
- Unrestricted Resource Consumption (DoS)
- Credential / Identity Confusion
- Broken Authentication / Authorization
These map directly to corresponding NIST control families (e.g. CM, AC, SC, SI) to guide which policies and tools should be applied.
2. Pre-runtime Controls
Pre-runtime (green box) controls are implemented before an API is deployed during planning, design, and build phases. They align to NIST SP 800-53 controls such as:
| Pre-runtime Control | NIST Control Family | Purpose |
|---|---|---|
| Maintain API Inventory with Ownership Mapping | CM-8 (System Inventory) | Gain visibility into every API and its owner |
| Annotate Fields by Sensitivity & Trust | PL-8 / PM-5 | Tag PII/PHI fields to drive downstream filtering |
Use Semantic Data Types (e.g., EmailAddress) | SI-10 (Input Validation) | Encode domain rules at schema level |
| Request/Response Schema Validation | SC-3 / SI-8 | Enforce shape, length, and format of payloads |
| Define API Specification (OpenAPI, gRPC, Thrift) | SA-22 (Developer Security Testing) | Serve as single source of truth for design and tests |
- Visibility & Inventory
- Establish a living catalog of APIs (CM-8).
- Data Labeling & Typing
- Annotate each field’s sensitivity (PM-5) and apply semantic types.
- Schema-Driven Validation
- Leverage machine-readable specs (SA-22) to auto-generate request/response checks.
3. Runtime Controls
Runtime (yellow box) controls defend every API call in production, mapping to NIST families such as IA, AC, SC, SI:
| Runtime Control | NIST Control Family | Purpose |
|---|---|---|
| Encrypt All API Traffic (TLS) | SC-8 | Ensure confidentiality and integrity in transit |
| Authenticate Services and Users | IA-2 | Verify client and user identities |
| Authorize Every Request to Resources | AC-3 | Enforce least-privilege access control |
| Apply Rate Limiting / Circuit Breaking | SC-5 | Throttle excessive usage and prevent DoS |
| Sanitize and Validate All Inputs | SI-10 | Reject malformed or malicious payloads |
| Field-level Authorization and Redaction | AC-6 / SC-28 | Mask sensitive fields based on role or trust level |
| Log API Access and Monitor Usage | AU-2 / AU-6 | Collect audit trails and detect anomalous behavior |
- Secure Transport
- TLS everywhere (SC-8) to prevent sniffing or tampering.
- Strong Identity & Access Controls
- Use OAuth2/OIDC, mTLS (IA-2) and enforce fine-grained resource policies (AC-3).
- Throttling & Resilience
- Rate limits and circuit breakers (SC-5) to mitigate DoS risks.
- Runtime Validation & Redaction
- Leverage schema and field annotations to sanitize inputs (SI-10) and redact outputs (SC-28).
- Audit & Detection
- Centralized logging and monitoring (AU-2, AU-6) to spot abuse or compromise.
4. How to Use the Matrix
- Assess Your Threat Model
- Identify which of the six API risks apply to your service.
- Select Controls
- For each risk, pick the pre-runtime and/or runtime controls listed.
- Map to NIST Controls
- Integrate the corresponding NIST SP 800-53 control requirements into your security plans and audits.
- Implement & Automate
- Embed schema validation, rate limits, auth checks, and logging into your CI/CD pipeline and API gateway.
- Monitor & Iterate
- Use audit logs and metrics to validate control effectiveness, then refine your API spec and enforcement rules.
Part 3 - Zero Trust API Communication Flow
The Zero Trust API Communication Flow diagram illustrates how modern cloud-native environments enforce identity, authentication, and authorization at every hop ensuring that no request is trusted by default. By canonicalizing credentials, leveraging both service and user identity providers, and inserting API gateways at the edge, perimeter, and egress, this flow implements a true Zero Trust posture.
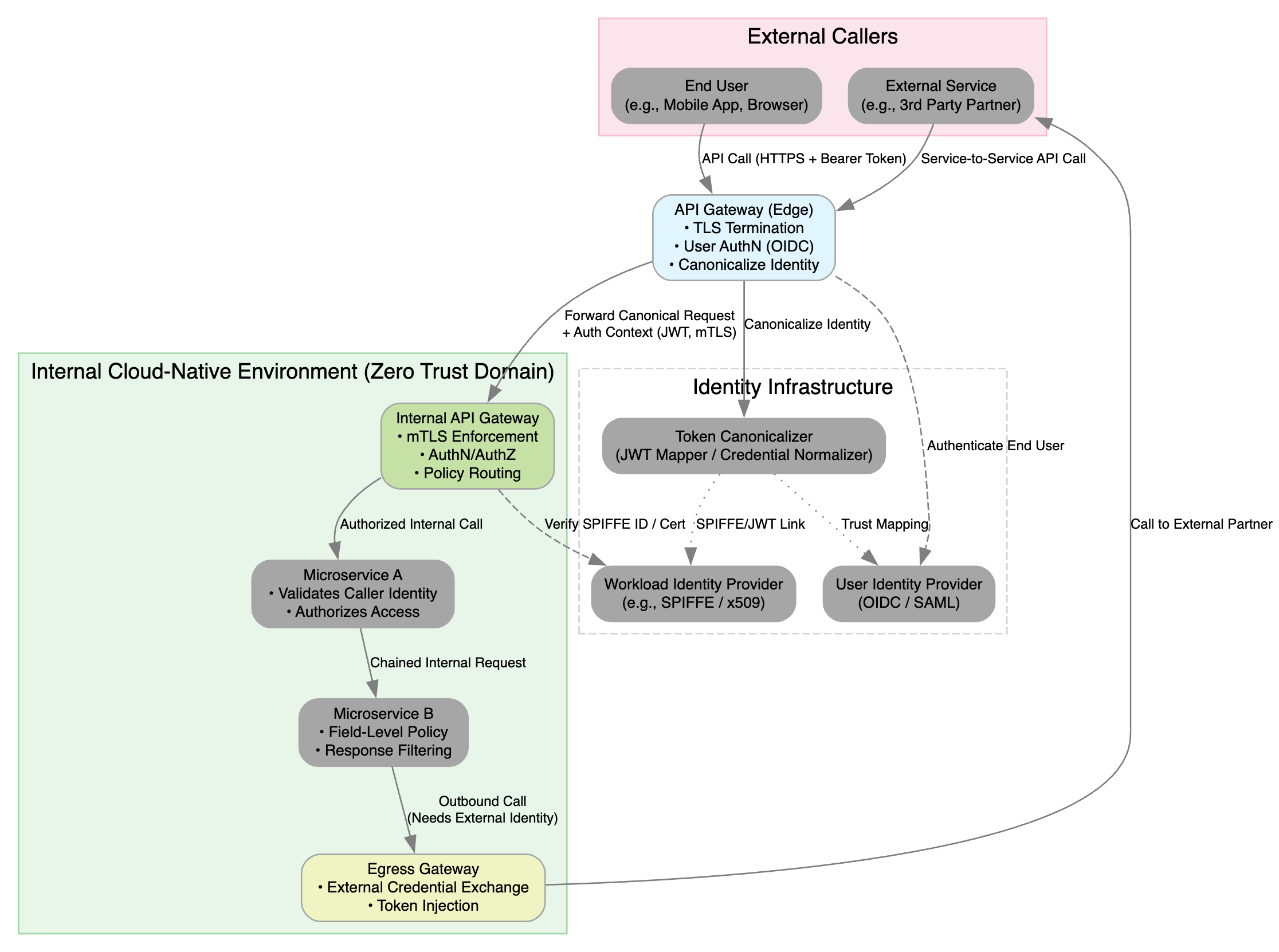
1. Purpose
- Demonstrate end-to-end identity enforcement for both human users and machine clients
- Canonicalize and normalize credentials (JWTs, mTLS certificates) into a single, trusted identity context
- Enforce policy at multiple gateway layers (edge, internal, egress) for defense-in-depth
2. Key Components
2.1 External Callers (Untrusted Perimeter)
- End User (Mobile App, Browser)
- External Service (3rd-Party Partner)
- Submit HTTPS requests with bearer tokens or client certificates
2.2 API Gateway (Edge)
- TLS Termination
- User Authentication (OIDC)
- Credential Canonicalization
- Maps OIDC tokens or client certs into a standardized JWT/mTLS identity
2.3 Identity Infrastructure
- Token Canonicalizer
- JWT Mapper / Credential Normalizer
- Workload Identity Provider (e.g., SPIFFE / x.509)
- User Identity Provider (OIDC / SAML)
- Trust Mapping
- Associates user identities with service identities
2.4 Internal API Gateway (Service Mesh Edge)
- mTLS Enforcement between gateways and services
- Authorization & Policy Routing based on canonical identity
2.5 Microservices
- Microservice A
- Validates caller identity, enforces coarse-grained access
- Microservice B
- Applies field-level policy, response filtering
2.6 Egress Gateway
- External Credential Exchange
- Obtains credentials suitable for downstream external partners
- Token Injection
- Wraps outbound requests with the appropriate canonical token
3. Communication Flow
- External Call
- User or partner service calls the Edge API Gateway over HTTPS with a bearer token or client cert.
- Edge Gateway Processing
- Terminates TLS, authenticates the user via OIDC, then canonicalizes credentials into a normalized JWT or SPIFFE ID.
- Identity Resolution
- The Token Canonicalizer consults the User Identity Provider (OIDC/SAML) and Workload Identity Provider (SPIFFE) to verify and map trust.
- Internal Call
- The Edge Gateway forwards the request (with canonical identity) into the Internal API Gateway, enforcing mTLS and policy routing.
- Service-to-Service Authorization
- Microservice A validates the caller’s identity and enforces route-level access. If allowed, it forwards the chained request to Microservice B.
- Field-Level Enforcement
- Microservice B applies fine-grained, field-level authorization and response filtering based on the canonical identity claims.
- Outbound to External Partner
- For any call that must exit the zero-trust domain, the Egress Gateway performs external credential exchange and injects the partner-approved token before dispatch.
4. Zero Trust Principles Realized
- “Never trust, always verify”
- Every ingress, egress, and east-west call is authenticated and authorized.
- Least privilege enforcement
- Policy decisions at gateways and services use canonical identity to enforce minimal access.
- Defense-in-depth
- Multiple layers of gateways and identity providers prevent lateral movement or credential spoofing.
- End-to-end visibility
- Canonical tokens carry a consistent identity context, simplifying audit and telemetry.
Part 4 - API Gateway Deployment Patterns
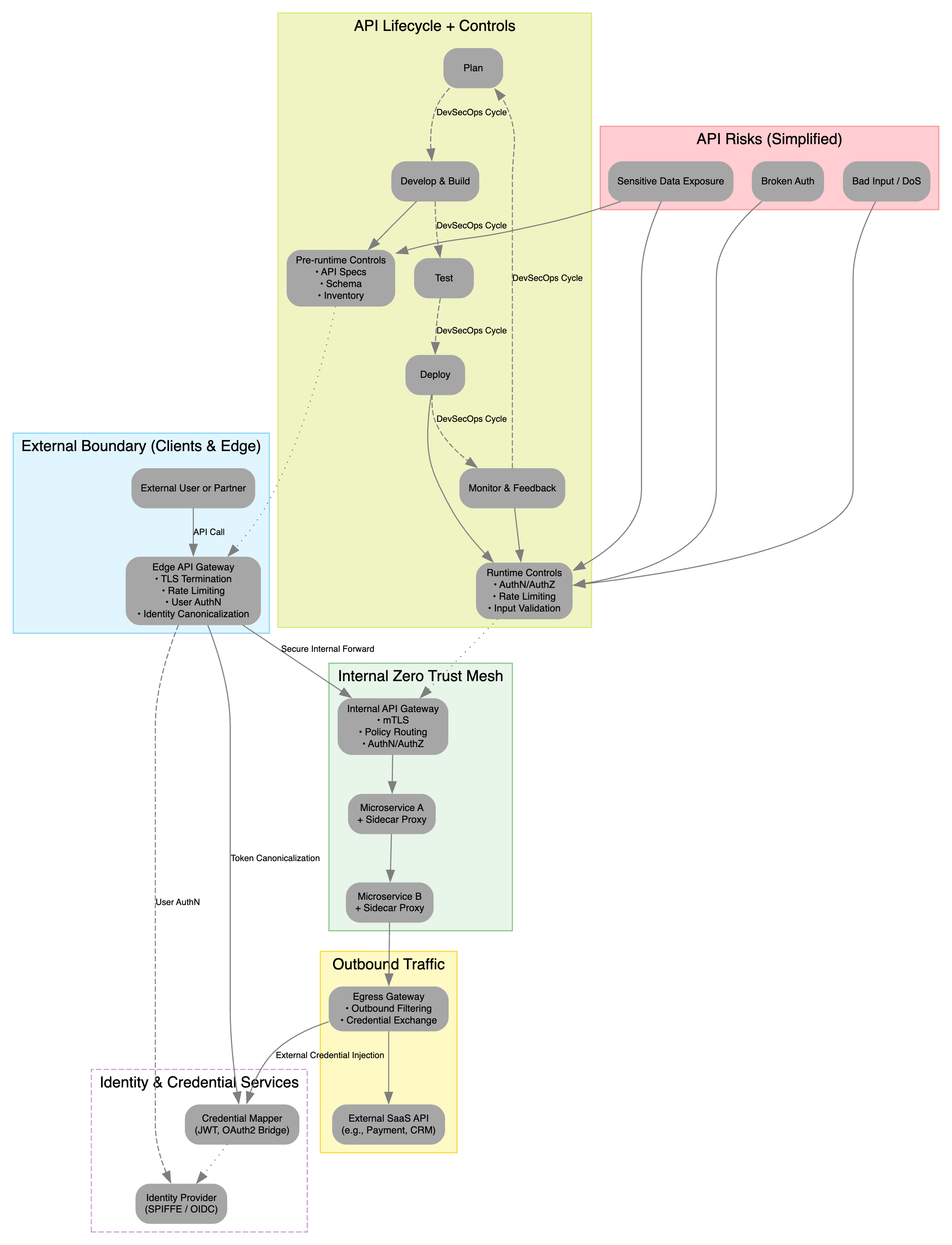
The API Gateway Deployment Patterns diagram shows how to position and configure API gateways and sidecar proxies across the external edge, internal service mesh, and outbound egress zones while relying on a central identity & credential infrastructure for seamless trust translation.
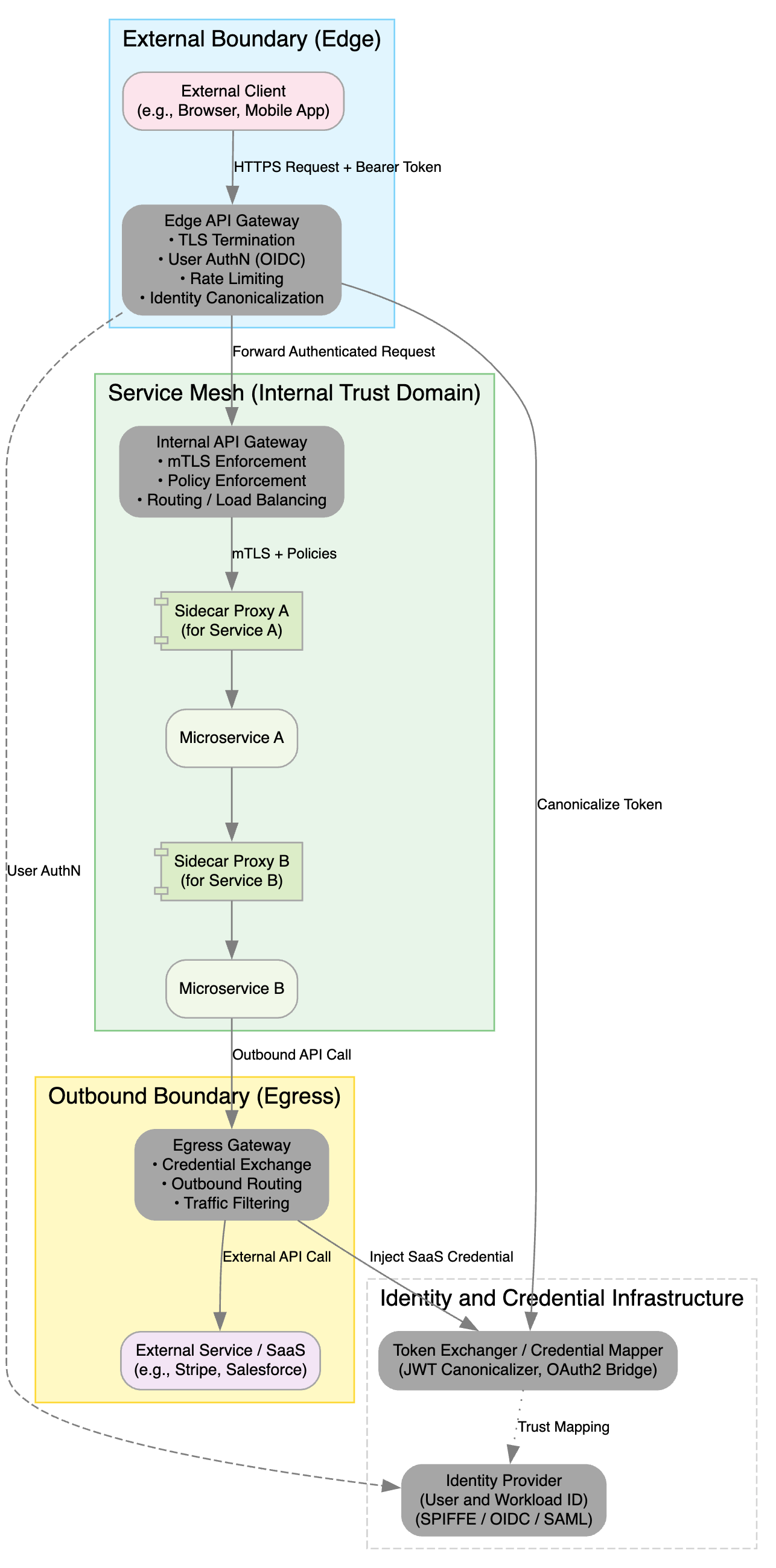
1. Purpose
- Visualize gateway placement at the edge, mesh-interior, and egress boundaries
- Highlight sidecar proxy integration for per-service policy enforcement
- Illustrate credential exchange flows for both inbound and outbound API calls
2. Deployment Layers & Components
2.1 External Boundary (Edge)
- External Client (e.g., browser or mobile app) sends an HTTPS request with a bearer token.
- Edge API Gateway at the perimeter:
- TLS termination
- User authentication (OIDC)
- Rate-limiting
- Identity canonicalization
This edge gateway offloads SSL and first-line access controls, normalizing tokens before traffic enters your mesh.
2.2 Service Mesh (Internal Trust Domain)
Inside the mesh, you combine an Internal API Gateway with Sidecar Proxies for defense in depth:
Internal API Gateway
- mTLS enforcement between gateways and services
- Global policy enforcement (authz, routing, load balancing)
Sidecar Proxy A / B (deployed alongside each microservice)
- Enforce per-service mTLS and fine-grained policies
- Inject or validate canonical tokens at the pod level
Microservices focus solely on business logic, trusting sidecars to handle security.
This layered mesh ensures every hop is authenticated and authorized.
2.3 Outbound Boundary (Egress)
Egress Gateway consolidates all outbound API calls (e.g., to Stripe, Salesforce):
- Credential exchange (OAuth2 bridge or JWT injector)
- Outbound routing and traffic filtering
Token Exchanger / Credential Mapper in the identity infrastructure:
- Transforms internal (SPIFFE/JWT) tokens into external SaaS credentials
Centralizing egress maintains strict control over what leaves your environment and how it’s authenticated.
3. Credential Exchange Patterns
- Canonicalization at Edge
- Edge gateway normalizes incoming OIDC tokens or client certs into a canonical JWT or SPIFFE ID.
- mTLS & Token Forwarding
- Internal gateway and sidecars propagate the canonical identity in headers over mTLS.
- Outbound Token Transformation
- Egress gateway invokes the Token Exchanger to swap internal identities for partner-acceptable credentials.
This pattern decouples your services from direct secret management and enables seamless trust mapping.
4. Best Practices
- Centralize Policy in the Mesh Control Plane
- Define rate limits, authentication, and routing rules once, and push them to gateways & sidecars.
- Leverage Sidecars for Uniform Enforcement
- Sidecars ensure consistent mTLS, auth checks, and observability without touching application code.
- Isolate and Monitor Egress
- Route all outbound calls through a single gateway to simplify logging, credential rotation, and egress-policy enforcement.
- Use a Unified Identity Fabric
- Adopt SPIFFE/OIDC across edge, mesh, and egress to maintain one trust root and streamline audits.
Conclusion
Effective API security is not achieved through a single control or tool it’s the result of aligning architecture, policy, identity, and enforcement across the entire lifecycle. By combining DevSecOps rigor, Zero Trust principles, and gateway-centric design patterns, organizations can confidently defend their APIs against modern threats. This unified framework provides the clarity and structure needed to assess risk, implement appropriate controls, and continuously improve security posture. Whether you’re securing internal microservices or exposing APIs to partners and customers, adopting these patterns ensures every API interaction is authenticated, authorized, observable, and resilient by design.
Reference
- I learned a lot from the NIST guide and then I simplified this guide into this blog - https://csrc.nist.gov/pubs/sp/800/228/ipd