
Introduction
Dead Drops are an interesting mix of art, technology, and espionage-inspired tactics. They started as a public art project but have evolved into a fascinating case for cybersecurity professionals. These are USB drives embedded in public spaces, like walls or structures, where anyone can access and exchange files offline. It sounds harmless, right? Well, not always.
From a cybersecurity perspective, Dead Drops can be both a curiosity and a potential threat. In this article, we will explore what Dead Drops are, how they can be exploited, what risks they pose, and what practical actions you can take if you decide to interact with them. If you are into advanced threat analysis and operational strategies, you are in the right place.
What Exactly Are Dead Drops?
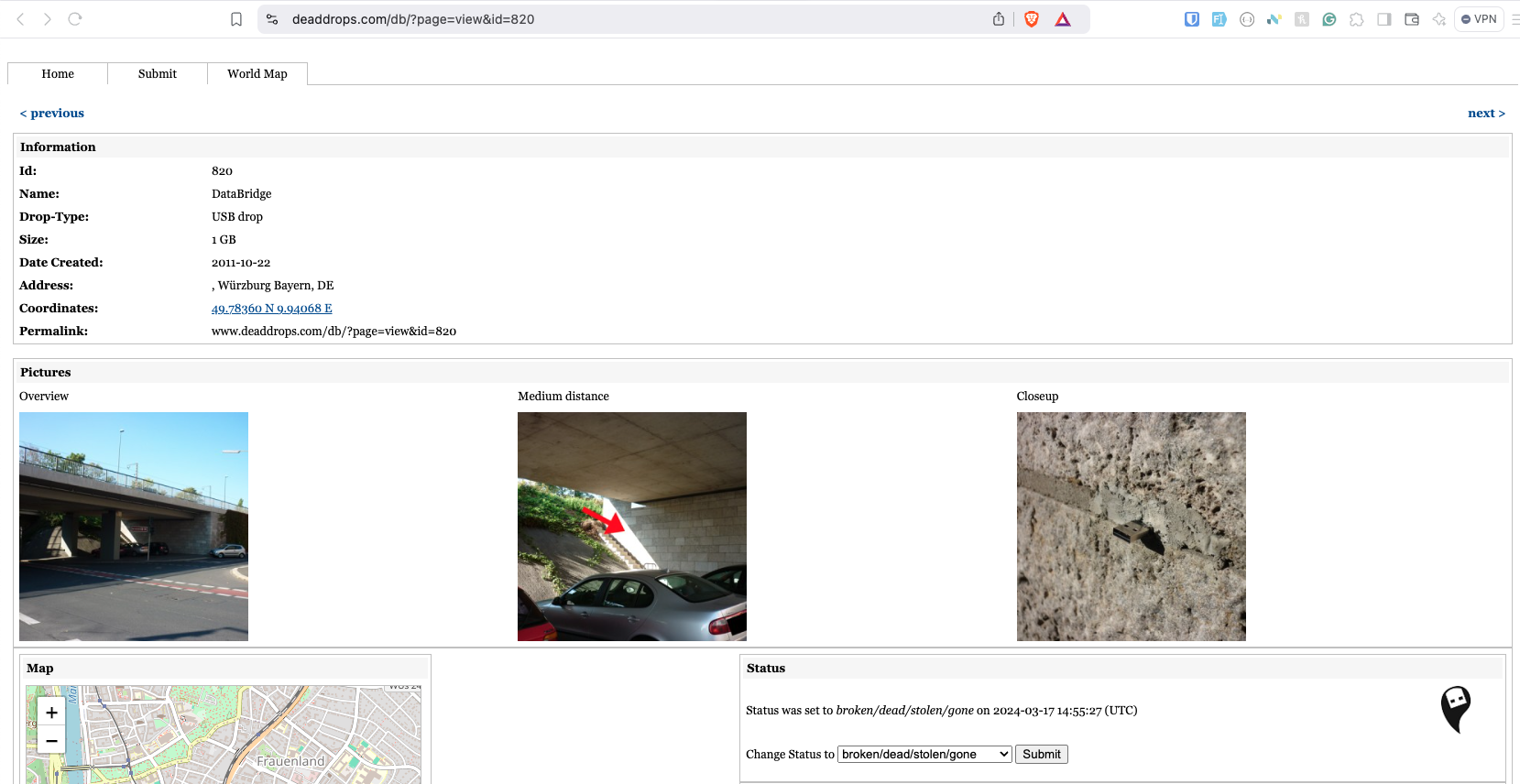
Dead Drops are essentially USB drives embedded in public spaces. They are part of an open-source initiative started by Berlin-based artist Aram Bartholl. The idea is to create an anonymous, offline file-sharing network. You can find these USBs in walls, bridges, or other public locations, plug in your device, and swap files.
While the concept is rooted in collaboration and anonymity, it has naturally drawn the attention of cybersecurity professionals, hobbyists, and unfortunately, malicious actors. The anonymity and offline nature of Dead Drops make them a playground for both ethical and unethical activities.
Why Should Cybersecurity Experts Care?
Dead Drops aren’t just a fun art projects but they are a potential threat vector. Here is why:
Malware Delivery: Imagine plugging a random USB into your system only to find it loaded with ransomware, spyware, or other malicious software. Dead Drops can serve as perfect distribution points for malware. If the drive includes autorun scripts, it can exploit vulnerable systems immediately.
Data Exfiltration: Malicious actors can use Dead Drops to offload stolen data or share sensitive information with others. Because this method bypasses digital networks, traditional firewalls and intrusion detection systems won’t catch it.
Espionage Dead Drops take a page straight out of a spy thriller. Intelligence operatives and threat actors can use them to exchange classified or operational data without leaving a digital trace.
Bait for Social Engineering: A malicious USB embedded in a wall is like digital candy for the curious. People can’t resist plugging it in, which creates opportunities for attackers to exploit organizational networks through unsuspecting individuals.
How Threat Actors Use Dead Drops
Dead Drops can serve a range of purposes for different kinds of threat actors:
- Hacktivists: Sharing propaganda, leaked documents, or sensitive files anonymously.
- Cybercriminals: Exchanging stolen data, financial information, or malicious tools.
- Nation-State Actors: Enabling offline communication between operatives.
- Insiders: Employees might use Dead Drops to smuggle sensitive data out of their organizations.
Practical Advice for Using or Investigating Dead Drops
If you are planning to interact with Dead Drops for research, curiosity, or ethical hacking, here are some things to keep in mind:
For Individuals:
- Always Use a Sandbox: Never use your personal or corporate devices to access a Dead Drop. Use isolated environments or virtual machines.
- Analyze Files Carefully: Extract metadata, check for hidden payloads, and compare file hashes against known malware databases.
- Monitor Threat Actor Discussions: Use OSINT tools to track mentions of Dead Drops on forums or in the dark web.
For Organizations:
- Educate Your Team: Train employees to avoid plugging unknown USB drives into their systems.
- Enforce USB Policies: Disable USB ports where unnecessary or use endpoint security solutions to monitor their use.
- Track Dead Drops Near You: Monitor public databases like DeadDrops.com to stay aware of potential local threats.

For Public Users
- Be Skeptical: If you find a Dead Drop, treat it as suspicious. Files on these drives could be malicious.
- Use Dedicated Hardware: If you are curious and want to explore, use a dedicated, isolated device.
- Check File Integrity: Use tools to verify file hashes and ensure nothing has been tampered with.
Websites and Resources for Dead Drops
If you are keen to explore or investigate Dead Drops, here are some resources:
- DeadDrops.com: A global map and database of Dead Drops locations.
- GitHub Repositories: Many repositories host tools for analyzing USB devices or files found on them.
- Forums and OSINT Tools: Platforms where security experts discuss and monitor Dead Drops.
Future Risks and Evolving Threats
As technology evolves, so do the risks associated with Dead Drops
- USB-C and Thunderbolt Exploits: Newer USB technologies might introduce new vulnerabilities.
- IoT Integration: Dead Drops could potentially target smart city infrastructure or IoT devices.
- Blockchain Nodes: Dead Drops could evolve into offline blockchain data exchange points, posing new challenges.
Conclusion
Dead Drops are an intriguing intersection of art, anonymity, and technology. While they started as a public art project, their potential misuse by threat actors is a serious concern. For cybersecurity professionals, Dead Drops offer a valuable case study in offline threat vectors. Whether you are analyzing them for research or building defenses against their misuse, understanding their risks and operational nuances is critical.