In today’s rapidly evolving threat landscape, traditional vulnerability management (VM) practices face significant limitations, creating gaps that leave organizations exposed to modern cybersecurity challenges. Attack Surface Management (ASM) emerges as a transformative approach that bridges these gaps, aligning security strategies with the pace and complexity of contemporary threats. This blog explores how ASM enhances traditional VM to create a more comprehensive and dynamic security framework.
From Traditional VM to ASM: A Comparative Analysis
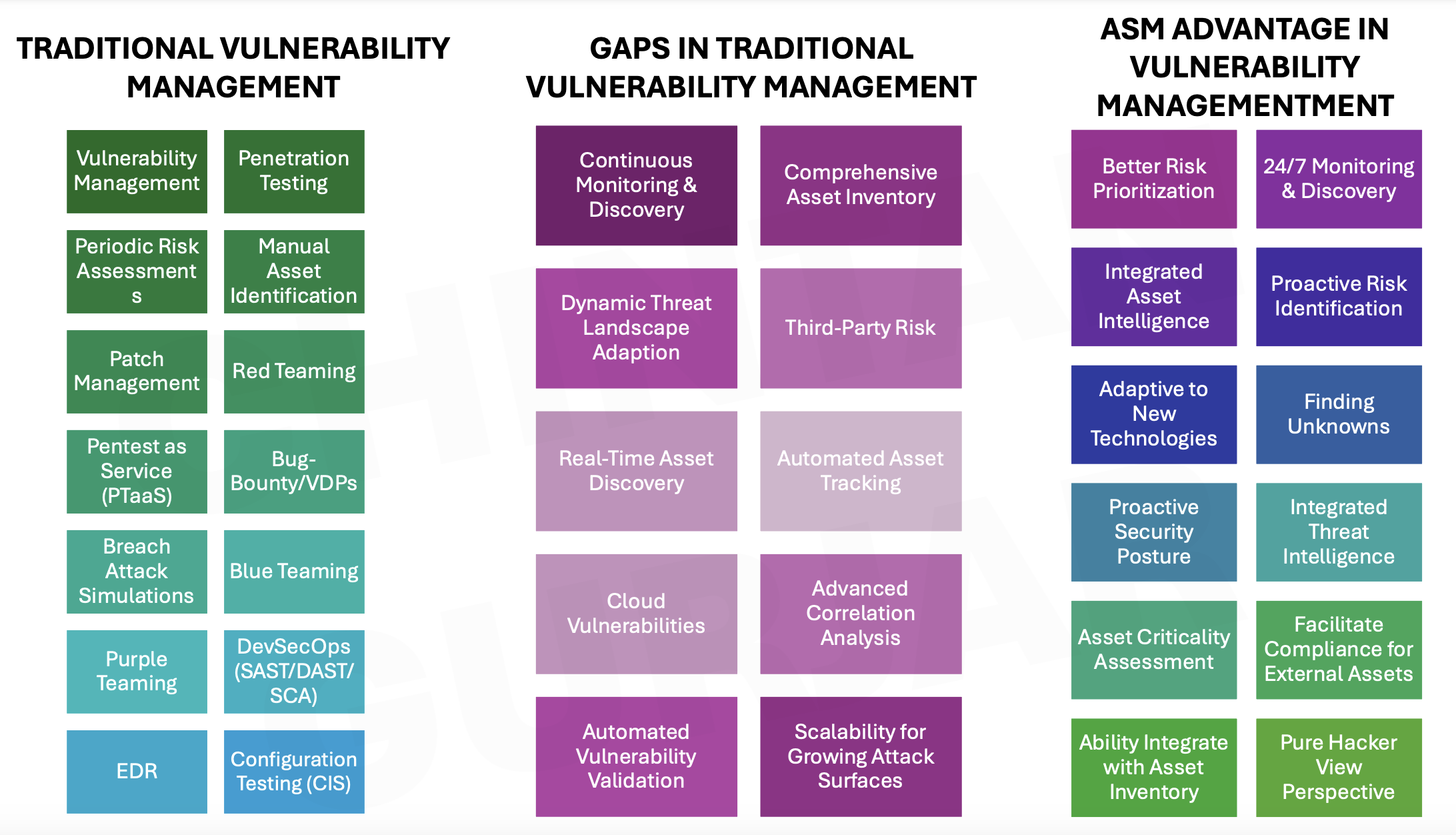
Traditional Vulnerability Management: Strong but Limited
Traditional vulnerability management tools and techniques form the backbone of cybersecurity programs. They focus on vulnerability identification, patching, and periodic testing to ensure known risks are managed. However, traditional VM is fundamentally reactive and struggles to scale with the ever-expanding attack surface. Key limitations include:
- Static Processes: Reliance on periodic scans and assessments that lack real-time monitoring.
- Manual Effort: Asset identification and tracking are often labor-intensive.
- Scope Restrictions: Limited ability to address third-party and cloud risks.
- Risk Prioritization: Focus on known vulnerabilities but misses emerging or unknown threats.
Bridging the Gaps with ASM
ASM addresses these limitations by introducing a more dynamic, proactive, and automated approach. It doesn’t replace traditional VM but complements it, ensuring organizations can meet modern challenges. Let’s explore how ASM directly fulfills the gaps:
Continuous Monitoring vs. Periodic Scans
Traditional VM is built on scheduled scans and assessments. ASM evolves this model with 24/7 monitoring and discovery, providing real-time visibility into the ever-changing attack surface.Comprehensive Asset Inventory
Manual asset identification in traditional VM often leads to incomplete inventories. ASM ensures a dynamic and automated inventory, tracking assets across on-premises, cloud, and third-party environments.Proactive Risk Identification
Traditional VM focuses on known risks. ASM shifts the paradigm with proactive discovery of unknown vulnerabilities, ensuring risks are mitigated before exploitation.Dynamic Threat Adaptation
ASM integrates real-time threat intelligence and adapts to emerging technologies, filling the reactive gap left by static traditional VM processes.Third-Party and Cloud Vulnerabilities
Traditional VM struggles to handle third-party risks and cloud environments comprehensively. ASM’s capabilities extend to third-party risk management and cloud vulnerability tracking, providing a holistic view.Advanced Risk Prioritization
Traditional VM often struggles with prioritizing risks effectively. ASM enhances this by combining criticality assessment with correlation analysis, ensuring organizations focus on the most impactful vulnerabilities.Scalability for Growing Attack Surfaces
As digital ecosystems grow, traditional VM tools lack scalability. ASM ensures organizations can handle expanding attack surfaces seamlessly, without added complexity.
Thought Leadership: Why ASM is the Future
The integration of ASM with traditional VM is more than an upgrade—it represents a fundamental shift in cybersecurity strategy. Organizations are no longer dealing with static perimeters; instead, the attack surface now spans multi-cloud environments, third-party vendors, IoT devices, and beyond. Here’s why ASM is the future of vulnerability management:
Hacker’s Perspective at Scale
ASM operates as if from a hacker’s point of view, identifying weaknesses and blind spots that traditional VM might miss. This “outside-in” perspective is crucial for modern security.From Reactive to Proactive
Traditional VM reacts to known threats; ASM anticipates and prevents risks by finding unknown vulnerabilities, ensuring an adaptive security posture.Operational Efficiency
By automating processes like asset discovery, risk prioritization, and threat intelligence, ASM reduces manual overhead and allows teams to focus on higher-value tasks.End-to-End Visibility
ASM provides an integrated view of all assets, vulnerabilities, and threats, ensuring nothing slips through the cracks. It complements VM’s internal focus with an external lens.Future-Proofing Security
With its ability to adapt to emerging technologies and integrate seamlessly with existing tools, ASM ensures that organizations remain resilient as their environments evolve.
Conclusion: A Unified Approach for Holistic Security
When viewed side by side, it’s clear that ASM doesn’t replace traditional VM but supercharges it. Together, they offer a unified framework that addresses not just today’s risks but tomorrow’s as well. By filling the gaps left by traditional approaches, ASM enables organizations to transition from a reactive to a proactive, scalable, and intelligent cybersecurity strategy.
The future of vulnerability management lies in this integration—a seamless combination of the proven methods of traditional VM and the forward-thinking capabilities of ASM. Organizations that embrace this evolution will not only close their security gaps but also position themselves as leaders in cybersecurity resilience.