Overview
In this blog post, I am sharing a detailed JWT Security Testing Checklist document I have created and found immensely valuable for penetration testers, developers, and security teams. This checklist provides a structured approach to identifying vulnerabilities in JSON Web Tokens (JWTs) implementations.
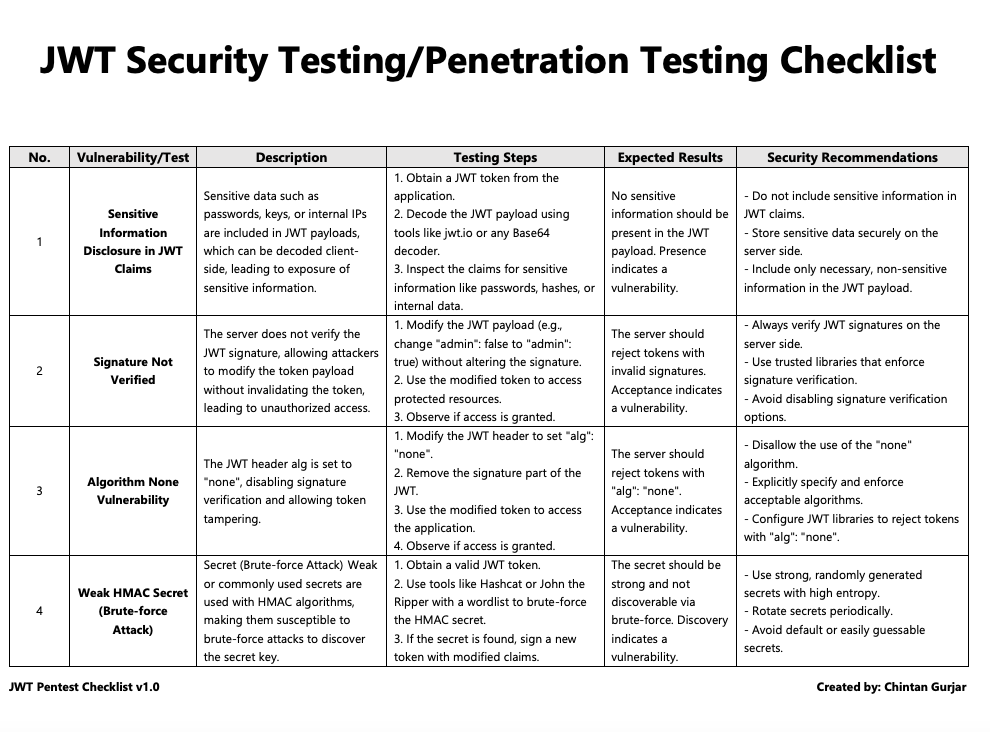
Sneakpeak of Checklist
Why Share This Document?
JWTs are widely used for authentication and authorization, but they can introduce serious vulnerabilities if not implemented securely. By sharing this checklist, I hope to provide practical guidance to developers and penetration testers, bug-hunters.
What’s in the Checklist?
The checklist covers 27 common vulnerabilities and their testing steps, expected outcomes, and security recommendations.
Download the Checklist
You can download the complete checklist directly from here: