Implement an Effective VIP Monitoring Program
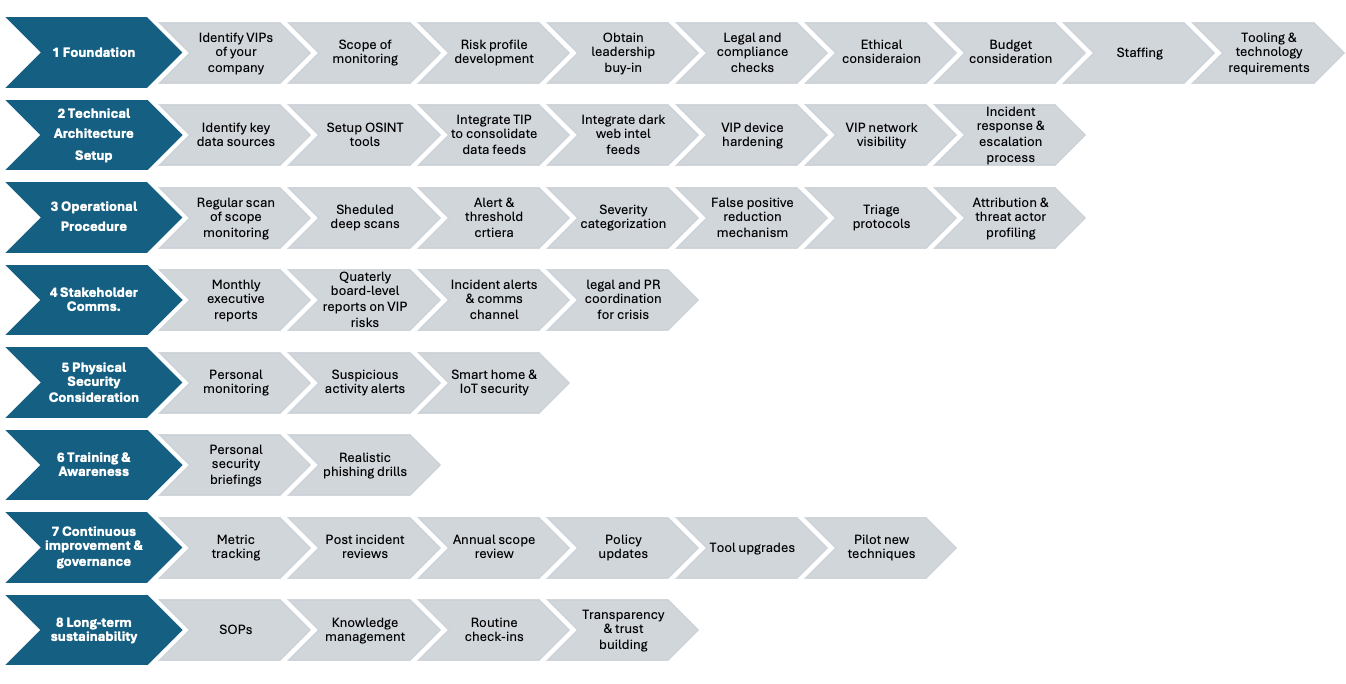
Monitoring high-profile individuals requires a methodical and structured approach. Below are actionable steps to design and implement an effective VIP monitoring program:
Step 1: Define the Scope and Objectives
- Identify VIPs: Determine the key individuals who need monitoring based on their roles, influence, or risk level.
- Set Clear Goals: Decide on the purpose of monitoring, such as protecting personal data, ensuring physical security, or preventing cyberattacks.
- Determine Threat Sources: Identify where threats might originate, such as social media, forums, dark web, or physical environments.
Step 2: Build a Monitoring Framework
Data Collection Sources:
- Social Media Platforms: Monitor mentions, impersonations, or hostile messages on Twitter, LinkedIn, Instagram, etc.
- Dark Web: Track potential leaks or exposed credentials on dark web marketplaces or forums.
- News and Media: Stay updated with mentions or headlines involving VIPs.
Monitoring Tools:
- Use automated tools like OSINT frameworks and social media analytics platforms to streamline monitoring efforts.
Reporting Mechanism:
- Establish a reporting framework to inform stakeholders of findings in a concise, actionable format.
Step 3: Mitigate Risks
Threat Prioritization:
- Classify threats based on severity and potential impact.
- Focus on immediate mitigation for high-risk threats.
Response Strategies:
- Engage with platform providers to remove malicious content or impersonation accounts.
- Strengthen security settings for VIP accounts, such as enabling MFA or account monitoring.
Incident Response Plan:
- Develop a detailed response plan for scenarios like data leaks, phishing attempts, or physical security threats.
Step 4: Continuous Improvement
Regular Audits:
- Periodically evaluate the effectiveness of your VIP monitoring program and identify gaps.
Update Protocols:
- Adapt monitoring strategies to evolving threat landscapes and VIP activities.
Stakeholder Collaboration:
- Work closely with VIPs, security teams, and legal departments to ensure comprehensive protection.
By implementing these steps, you can proactively safeguard VIPs against emerging threats, enhancing both their security and the organization’s resilience.