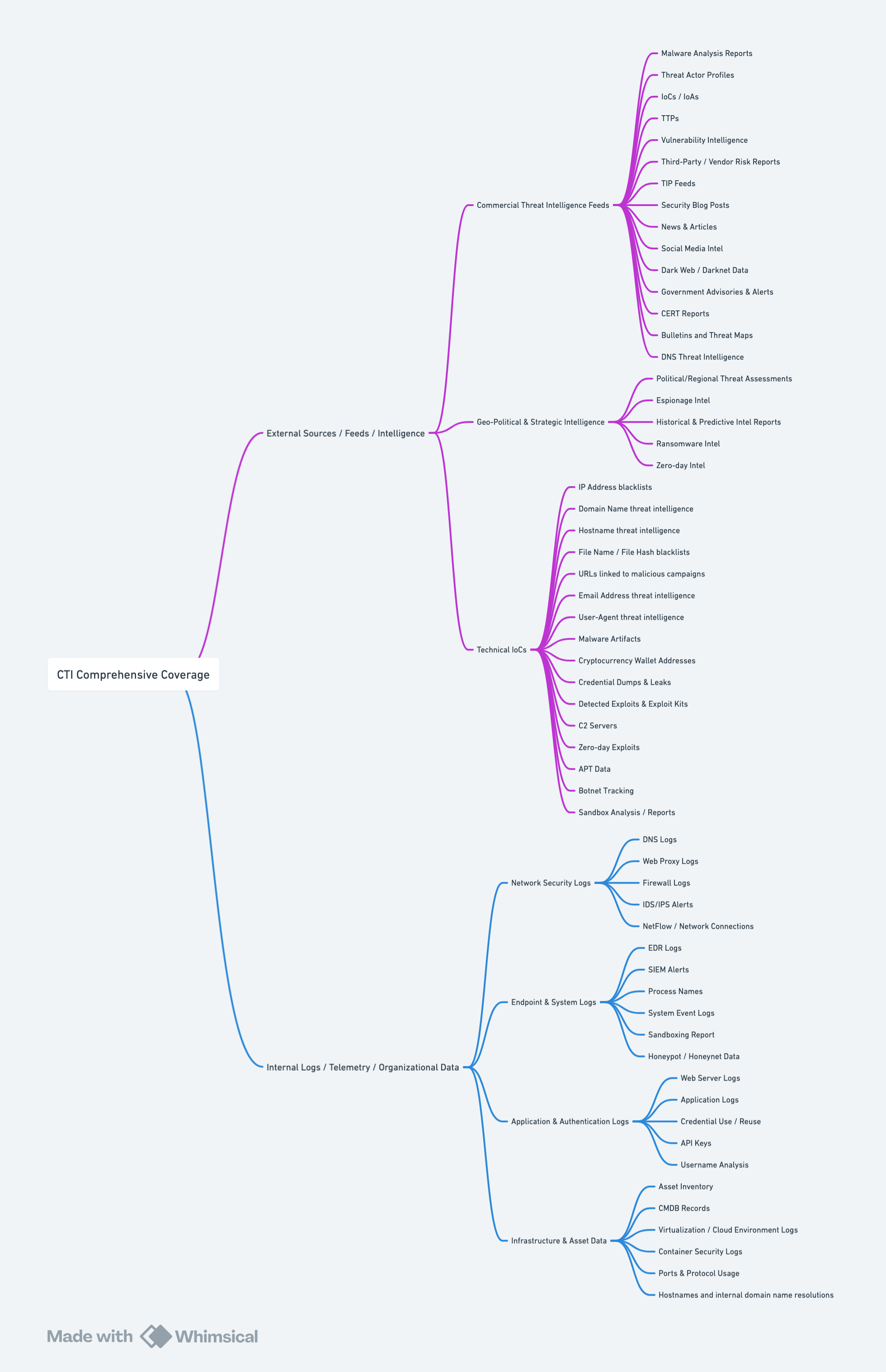
Effective cyber threat intelligence isn’t just about collecting random feeds or logging bits of data—it’s about having complete coverage. By gathering external intel (like commercial feeds, open-source reports, and real-time Indicators of Compromise) and pairing it with internal data (such as DNS logs, endpoint alerts, and application activity), organizations get a full picture of potential threats. In this blog post, we’ll focus on the coverage side of a mature CTI program—pinpointing the most important intel sources and data points you need for a strong defense and quick response.